Criminalizing Dissent: Contested Evidence Introduced in J20 Trial Testimony
Washington, DC – The first trial of people mass-arrested during protests against Donald Trump’s Presidential Inauguration on January 20, 2017 is well underway. Jurors are continuing to hear testimony from prosecution witnesses called by Assistant US Attorneys Jennifer Kerkhoff and Rizwan Qureshi.
The current trial group of defendants consists of six individuals, including two medics and one journalist, who were caught up in the indiscriminate mass arrest on 12th & L streets in DC on Donald Trump’s inauguration day. None of them are alleged to have committed any acts of property destruction or violence, but the prosecution claims that through their alleged conspiracy with “the group” they can still be held responsible.
The most recent hearings have seen three major components of the case established by the prosecution. An undercover officer testified to his recollection of planning meetings and protests that he attended. A detective also recounted his work extracting information from defendant’s phones, and details of cell data was scrutinized. Jurors also began to hear from the police commander who was responsible for ordering the mass arrest on January 20.
Testimony on Wednesday, November 29 picked up where Tuesday left off. The defense completed their cross-examination of the testimony of DC Police officer Bryan Adelmeyer, who had been sent in undercover to infiltrate “Disrupt J20” planning meetings for anti-Trump protests on inauguration day. Adelmeyer was questioned about different details of the January 8 “Disrupt J20” meeting that he attended in a church basement.
Mostly at issue was a video of the meeting, provided by Project Veritas and recently submitted into evidence by Assistant US Attorney Kerkoff. (Defense attorneys had not yet cross-examined Adelmeyer when the video was introduced during his direct testimony the day before.) When asked if the Project Veritas video had been checked by an expert for signs of tampering, Officer Adelmeyer said he didn’t know.
The defense then played portions of the video in which the timer at the bottom either jumped ahead in time or suddenly disappeared, demonstrating that the recording had been altered in some way. It was also pointed out that the government had admitted to editing the video to hide the identity of the Project Veritas employee who provided it.
Officer Adelmeyer admitted that he did not know if other Project Veritas members were at the meeting, raising the possibility that the far-right fake news entity, which boasts of using “entrapment journalism”, planted people in the video to say things which are now being used in court as evidence of conspiracy. When pressed by the defense, Adelmeyer also stated that he had been unaware that Project Veritas founder James O’Keefe pleaded guilty to “entrance under false pretenses” in 2013 after he allegedly broke into a Democratic Senator’s office.
The next witness was Detective David Evans. Evans said his job immediately after inauguration day, along with US Attorney Special Agent John Marsh, was to extract as much information as possible from cell phones and other electronics seized from those arrested at 12th & L streets. Evans stated that he used a Universal Forensic Extraction Device (UFED) made by the Israeli company Cellebrite to “download basically everything inside the phone.”
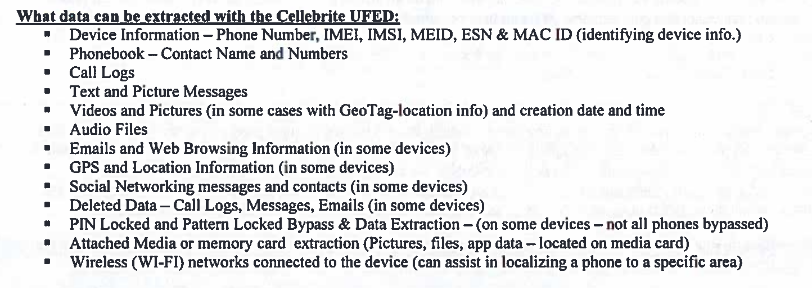
Extraction reports taken from each of the defendant’s phones was then presented. Information displayed on monitors in open court included detailed information about the specific Android phone (SIM, IMEI #, etc) as well as the defendants’ hotspot passwords and whether location services were enabled.
Detective Evans clarified that on phones with encryption enabled, he was only able to access basic device information and not the contents of the phone storage. (iPhones have encryption enabled by default, while many Android devices do not.)
One Cellebrite extraction report showing data taken from one defendant’s cell phone reportedly contains over 10,000 pages. In early 2016, we published an investigation detailing how data taken from phones by police using Cellebrite UFED devices is often then fed into NSA-preferred intelligence software to map out social networks.
Assistant US Attorney Kerkhoff proceeded to show emails and texts sent to a phone seized from a defendant. She offered emails containing basic information meant for street medics, as well as a jail support form, and asserted they were evidence of a premeditated criminal conspiracy. A short exchange of texts between two defendants who were arrested in the kettle at 12th & L just a few minutes after they arrived at the march, gave insight to the prosecution’s case.
The following messages were cited by Assistant US Attorney Jennifer Kerkhoff as evidence of a conspiracy because the messages show “their efforts to get her [the defendant] with the group and her efforts to join the group.”
-“Marching down 13th now.”
-“Coming”
-“I’m on Rhode Island and 1100”
-“I’m chasing y’all down 13th”
-“Turned on K”
Assistant US Attorney Kerkhoff made statements that seemed to claim that by continuing to seek out the protest march despite seeing a “trail of destruction” (Kerkhoff’s words) behind it, defendants in this text exchange were therefore involved in a conspiracy with the people who caused the damages.
The majority of texts and emails the prosecution showed from seized phones contained basic dispatch messages such as ‘medics needed in this area’ or other logistical info about time and location of different protest events, such as the locations of blockade actions at inauguration checkpoints. Other texts showed street medics discussing whether or not they would wear red tape identifying themselves at different protest events scheduled throughout Inauguration day.
No cell phone data provided as evidence in Wednesday’s hearing appears to have any bearing on the current defendants, except to show that some of them were either receiving updates about basic protest logistics or discussing in real-time their efforts to locate and attend a protest march.
Brett Cohen, defense attorney for Alexei Wood, a photojournalist who is currently facing a felony prosecution for covering the Trump inauguration protest, stated that DC Police seized several items of media equipment from Mr. Wood.
Before Judge Leibovitz ended court for the day, DC Police Commander Keith Deville began to testify. Deville was in charge of ‘Civil Disturbance Response’ on Inauguration Day & reportedly issued the order to carry out the indiscriminate mass arrest at 12th & L.
In what little testimony he did give before the clock ran out, Deville seemed to demonstrate a personal bias against anarchist protesters, saying “this particular group was going to be problematic … they were anarchists.”
DC Police Commander Deville's limited testimony in court so far seems to support the claim that he targeted the 'anti-capitalist and anti-fascist' march for an abusive mass arrest based on the group's political beliefs pic.twitter.com/4Bs1uQEYZe
— UNICORN RIOT (@UR_Ninja) November 29, 2017
Police radio from January 20 was played, along with a video compilation of helicopter footage, included a revealing exchange between Deville and an unknown subordinate. Asking about a different group than the group of people in and around the anticapitalist and antifascist march whose mass-arrest he would order, Deville said “Is that group anarchist-type or just protests[sic]?” to which the DC police officer replied, “There’s some anarchists but they’re not all anarchists.”
Commander Deville’s testimony is expected to continue at length on Thursday, November 29. Our previous post: Trials Begin for Trump Inauguration J20 Protests
To help our volunteer-operated, horizontally-organized, non-profit media collective please consider a tax-deductible donation:
J20 Trial Coverage & More:
- Criminalizing Dissent: Trials Begin for Trump Inauguration J20 Protests - November 29, 2017
- Criminalizing Dissent: Contested Evidence Introduced in J20 Trial Testimony - November 29, 2017
- Police Commander Behind J20 Arrests Joked About Holocaust, LGBTs - December 3, 2017
- Criminalizing Dissent: Trump Inauguration Protest Trial Enters Fourth Week - December 9, 2017
- Criminalizing Dissent: After Proving “Mere Presence” J20 Prosecution Rests Case - December 13, 2017
- Jury Finds Six #J20 Defendants “Not Guilty” on All Charges - December 21, 2017
- Interview: 188 Still Face Decades In Prison For Trump Inauguration Protest - January 13, 2018
- DC Mayor, Police Refuse to Release Financial Records of Trump Inauguration Investigation - January 17, 2018
- US Attorney Drops 129 Trump Inauguration Protest Cases, 59 Still Face Decades In Prison - January 18, 2018
- Second Trump Inauguration Protest Trial Begins - May 16, 2018
- Prosecutors Illegally Withheld Evidence From Trump Inauguration Protesters, Judge Finds - May 23, 2018
- Second J20 Trial Heads To Jury Despite Court Sanctions Against Prosecutors - June 1, 2018
- More Trump Inauguration Protest Arrestees Have Charges Dismissed - June 4, 2018
- Another Trump Inauguration Protester Acquitted at Trial - June 6, 2018
- Second Trump Inauguration Protest Trial Ends In Acquittals/Mistrials - June 7, 2018
- Federal Prosecutors Drop Eight More Trump Inauguration Protest Cases - June 13, 2018
- US Attorney Drops Remaining Trump Inauguration Protest Charges - July 6, 2018
DC J20 Protest Coverage:
- FERC Protest, Evict the DNC, & Disrupt the DeploraBall on the Eve of Trump’s Inauguration - January 23, 2017
- “No Peaceful Transition” for Trump as Thousands #DisruptJ20 in Washington, D.C. on Inauguration Day - January 27, 2017
- 214 Indicted on Felony Riot Charges for Protesting Trump Inauguration - March 15, 2017
- Anti-Racist Coalition Rallies Against Fascism and State Repression at DC Police HQ - June 25, 2017
- Protesters Face 80 Years as US Attorney Brings Unprecedented Mass Felony Charges (Includes Interview with Olivia, a Defendant) - June 29, 2017
- J20 Defendant Dane Powell Sentenced to Four Months in Federal Prison - July 7, 2017
- J20 Indictment Challenged in Motions Hearing; One Count Dismissed - July 28, 2017



