Hackers on Planet Earth Convention Unlocks Digital Secrets in NYC
New York City, NY – The Hackers on Planet Earth (HOPE) convention, organized by the hacker magazine 2600, is underway at the Hotel Pennsylvania. The convention has brought together hundreds of technologists and policy experts since 1994 and this year’s gathering, “The Circle of Hope: A Hacker’s Dozen” marks the 12th.
The convention schedule is jam-packed with sessions that go on until midnight, and Hope talks are livestreamed from three rooms: Vaughan, Booth and Ritchie with talks listed on a grid schedule. The convention is also broadcast worldwide via the HAM radio station Radio Statler; it also features tables from various groups and dozens of workspaces equipped with soldering irons.
Unicorn Riot reporters are on site talking with participants and collecting information on a wide range of topics. Some notable highlights from Friday’s sessions are below.
At the #hopeconf https://t.co/kD7GavzZQY pic.twitter.com/xlGoq6ZSkb
— John Huntington (@jhuntington) July 20, 2018
Torrent More Pharmaceutical Drugs: File Sharing Still Saves Lives
Michael Laufer from the Four Thieves Vinegar Collective presented several open source medical products, developed with a view towards resisting copyright and patent control. Four Thieves Vinegar Collective emerged from the underground and became public at the 11th HOPE conference in 2016, where they debuted Apothecary Microlab, an “open source automated chemical reactor designed to synthesize the active ingredients of pharmaceutical drugs.”
The Collective was able to leverage machine learning from a vendor that scanned several centuries worth of chemistry research, which helped them develop the most safe processes for independently creating medical drugs from precursors. The Collective has also released plans for a $30 EpiPen alternative called EpiPencil.
A recurring theme of the talk was the crisis around opiates and naloxone overdose reversal drugs. Since naloxone is manufactured from a heavily monitored base material that can also create opiates, Laufer showed that black market Oxycontin can also be converted into naloxone, which he provided to someone in the audience who thought they might need it to help others in the future.
Other technologies, such as 3D printing of medical device designs and free circuit boards were also introduced during the talk, as well as a file format resembling Python and YAML formats to control the hardware that can synthesize drugs from base materials.
“Cancer is not a big data problem,” said Laufer. “It’s your cancer — individualized” and thus treatment requires an individually tailored solution. In Laufer’s view, power in medical technology hinges on a kind of curation, while monopolies control access. It’s illegal to make and sell drugs if someone else holds the patents — treatment tends towards hooking “you into a system so that you have to pay.”
In fact, Laufer said, you can buy pre-cursor chemicals, “get a good scale” to measure ingredients, and perform simple reactions. Earlier in the work, a company called Chematica had assisted the Collective but this tapered off after it was purchased by the pharma giant Merck, raising costs to untenable levels. Laufer pointed out that science is a “human right” and “discovery happens no matter what is legislated.”
He encouraged attendees to photograph and distribute the following slide, entitled “Data sometimes ‘falls from a truck’.” Seemingly drawn from the Elsevier publishing empire’s Reaxys service, the data remains scrambled in several parts and could provide valuable aid to research.
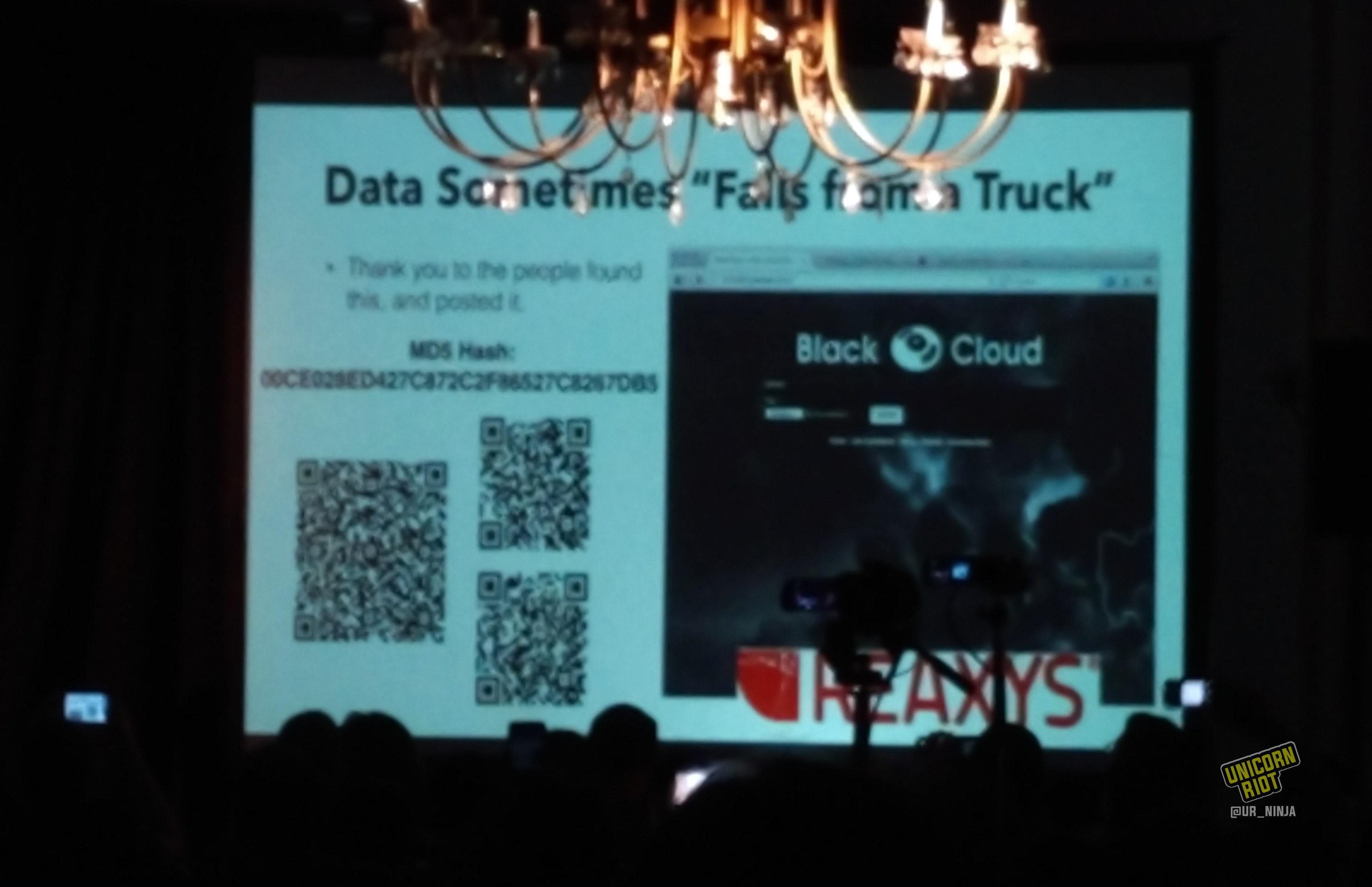
Laufer said that he had helped organize deals with heroin dealers to cut an anti-HIV prophylactic drug into their product, effectively reducing the risk of catching this deadly disease from shared needles.
Laufer pointed out that the RU-486 abortion induction drug can be converted into the increasingly hard to obtain hormone estradiol. He told the audience that “the medical industry is a war against the poor” – citing a recent incident in Boston’s MBTA system where a woman asked not to get an ambulance after her leg was mangled.
“Orphan drugs” are those that serve very limited populations and are often extremely expensive, despite their ordinary origins. Glybera, which consists of trillions of viruses, costs $1.2 million for an annual course of treatment. Soliris costs $700,000 a year; Elaprase, Naglazyme and Cinryze are among the most expensive orphan drugs. The FDA grants these patents for four times longer than the standard patent life for drugs which are made from relatively simple precursors such as enzymes, a component of human blood, and E. Coli. The engineering costs to improve drugs like these after they’ve been invented is “nominal” said Laufer.
Laufer added that he was soon going to obtain genetically engineered samples of strep mutans, the universally present bacteria which causes dental cavities by making lactic acid from sugar. The “biohacked” strep creates ethanol instead of lactic acid. Laufer promised if you get the new strep bacteria, you’ll never have a cavity again.
The Right to Repair Panel
“The Right to Repair” is a shorthand way to describe making sure that manufacturers can’t punish the repair industry for fixing devices like phones, tractors and appliances. Two experts on the policies, Gay Gordon-Byrne from the Repair Association and Nathan Proctor (@nproctor) from The US Public Information Research Group (US PIRG), governing the repairs of sophisticated devices broke down the political situation of “Right to Repair” organizing. There’s an effort across the US to push back against original equipment manufacturers (OEM) who seek to protect their shareholders’ interests by making it more difficult to repair devices like autos and tractors, using restrictive legal instruments like copyrights and contracts.
The Right to Repair rests on several major pillars including service manuals, parts, tools, firmware, and diagnostics. Massachusetts passed an extensive Right to Repair law via the general election ballot, with six-to-one support. Since these laws encourage repair customers to visit from adjacent states, they believe that good policies in a few states can rapidly spread to others — the very outcome OEM companies are lobbying hard to avoid.
Gordon-Byrne and Proctor believe many big corporations would prefer that everyone be managed by End User License Agreements (EULA) – more like licensed users than owners, to keep shareholders as happy as possible. Gordon-Byrne characterized this as a “circular monopoly” replacing the traditional idea of ownership. Motherboard produced a short documentary about farmers hacking their tractors which they found illustrative.
The prevailing inability to repair, for example, Apple iPhones, contributes to today’s situation where 416,000 smartphones get discarded in the United States every day. A third of the world doesn’t have access to smartphone technology, and companies like Apple are unwilling to let other parties service their devices.
Yet in general the Right to Repair is fully legal. You can’t copy software and sell it, said Gordon-Byrne, but the situation is made worse by lies deterring repair.
The policy approaches governing technology can be effectively divided along the contracts versus copyright line. Contracts are a state-level matter involving business law, ownership, and unfair and deceptive practice regulation. Copyright is a federal matter, regulated by the US copyright office, with licensing instead of ownership and device control via Digital Rights Management (DRM).
Gordon-Byrne and Proctor talked about the importance of the US Copyright Office to carve out exceptions to the Digital Millennium Copyright Act (DMCA). With lobbying efforts there has been a lot of success (studies through that office helped bolster the case for Right to Repair as well.)
At the state level, lobbying has been difficult because legislators are afraid of being blamed for hacking (for example, the industry has portrayed someone repairing batteries as an avenue for violating personal privacy in smart devices, while bad manufacturer design is almost always a much more severe risk). This has made efforts to build durable coalitions led by US PIRG and its state-level federated affiliates a critical element in fighting the OEM manufacturers who are trying to curtail the Right to Repair.
Hacking Healthcare: Bringing a Hacker Mindset to Solving Healthcare’s Biggest Problems
A talk by Dave Arney covered the tricky environment in the healthcare industry for cross-connecting lifesaving technologies and collecting usable data in order to make ‘dashboards’ with live information reducing errors that kill thousands of people annually.
Patients in evidence-based medicine still suffer from many preventable errors, with medical errors now forming the #3 cause of death in the United States, causing over 200,000 fatalities a year.
Improving this situation is a “wicked problem,” involving both social and technical factors. The lack of interoperability between machines is a major barrier in innovation that leads to many deaths from known causes. A lot of clinical actors are misaligned, and the lines between consumer and professional settings are becoming blurred as more advanced hardware becomes available in home settings.
The process of hooking up these devices, which often use proprietary data formats and cumbersome server and Internet access requirements, is quite complicated. Arney and his associates developed a method using small devices similar to a Raspberry Pi called BeagleBones, placed in discreet black boxes on the back of existing devices and connected via a serial cable, to collect data reliably.
Alternative solutions, such as power over Ethernet, raised biomedical electrical safety testing concerns. Routers all over the hospital would have to be tested for electrical safety in order to implement this approach.
Another major challenge is how most medical devices in hospitals are not synchronized to an accurate time, which makes determining cause and effect very difficult to establish.
Arney showed some examples of OpenICE, an Integrated Clinical Environment, which implements ASTM 2761-09-(13). The standards tend to be developed by manufacturers — not clinicians or patient advocates. OpenICE uses MongoDB and nodeJS for underlying displays and can provide useful visualizations.
Major challenges in working with medical devices also include how they generate a lot of inaccurate and noisy data. This leads to a lot of false positives triggering alarms, which leads to alarm fatigue among clinicians. Digital signal processing algorithms can detect false alerts.
Finally, Arney pointed out that the reluctance among manufacturers to provide secure connectivity actually causes more preventable deaths among patients by making health problems harder to detect overall, especially if better time synchronization and applications leveraging the data were available.
Sex Worker Rights and Internet Freedom
“If you don’t have a spot at the table, then you better bring your own chair.”
Mmmhm ?? So glad to be part of this full room of people at @hopeconf listening to @MsMaggieMayhem speak on sex work, censorship, and the need for decriminalization ? pic.twitter.com/AZlrtVZD2v
— yuan at hope conf (@ystvns) July 20, 2018
Around lunchtime, sex worker rights organizer Maggie Mayhem explained the impact of recent SESTA (“Stop Enabling Sex Traffickers Act”) legislation which curtailed an existing law called Section 230 of the Communications Decency Act, that protected Internet publishers from liability from the activities of members on the site. This, in turn, knocked lots of sex workers effectively off the Internet.
Without access to advertising providers, the new law caused many sex workers to have to seek clients on the street. On the streets, sex workers lack relatively safe Internet-based screening methods, and are more far vulnerable to assault and murder. It also means that people involved in “sex work“, broadly defined to include things like erotica and burlesque performances, are at a much higher risk of getting banned from social media.
The police are now using more intelligence gathering, including reverse image searches, automated license plate readers (ALPRs) closely targeted at certain sections of cities, and racially biased sting operations in sex work law enforcement activity. In some cases, law enforcement has used automated bots posing as sex workers.
Mayhem pointed out that sex workers have been able to use Internet message boards to improve working conditions and deal with inappropriate client behavior. She also covered how decriminalization of sex work has panned out in different jurisdictions. This talk covered a great deal of the major issues facing sex workers this year, amid a climate of increasing censorship that seems likely to continue.
See also Unicorn Riot’s related February 2018 report, Minneapolis Sex Workers Legal Training Mitigates Super Bowl Crackdown Fears
Crossing the Border in the Age of Trump
Bill Budington and Kurt Opsahl provided a primer from the Electronic Frontier Foundation on the latest trends in US border control. In recent years, more devices like Cellebrite systems have be used to extract data from smartphones at the border and in airports. The talk also covers tools and techniques to protect traveler data, so that, for example, the amount of data that can be extracted is minimized.
See a December 2017 Unicorn Riot interview with Bill Budington here covering the repeal of Net Neutrality
Social Engineering
A traditional feature of HOPE is the Social Engineering session with Emmanuel Goldstein and other 2600 Magazine regulars. They discussed various tactics and experiences including breaking into a communications satellite using phone phreaking, and briefly demonstrated in a live phone call how to handle a fake Gmail support service.
It Takes a Village to Hack a Voting System
A panel including Matt Blaze, Harri Hursti and Sandy Clark looked at the overall problem of secure elections, diving in to a close view of the many technical vulnerabilities in US voting machines.
Requirements for fair elections laid out by Blaze included public confidence in the outcome, and convincing the loser that they lost fair and square. Many technologists are skeptical of using computers extensively in many parts of the election process.
Secrecy and transparency are two competing interests in the design of elections. In the case of foreign actors intervening in elections, “disruption is sufficient.” The US federal government sets broad standards; elections are run by counties, which can be complex with several ballot types.
Upon examination, many voting machines in the past have had very serious problems including buffer overflows. A special exception in the Digital Millennium Copyright Act (DMCA) helps with ensuring that testing security in voting machines is fully legal.
At last year’s DEFCON conference in Las Vegas, a voting machine hacking village showed that the community could pick apart the voting machines and identify lots of vulnerabilities in commonly used models.
The DEFCON hacking village discovered secrets more quickly than the researchers had uncovered in prior years. The crowd was very good at finding vulnerabilities, including a secret WiFi interface nobody had found before then. Wireless attacks at the DEFCON village were developed in a few hours. They were even able to add Rick Astley ‘rickrolls’ to e-pollbooks, the registries of eligible voters in a locality.
The panelists from Nordic Innovations Labs explained how they started analyzing voting machine flaws in 2005 and in the 2007-2008 era they figured the identified vulnerabilities would be fixed. Instead, in many cases there have been no patches. In one report spanning 316 pages with two or three vulnerabilities per page, very little has been fixed.
The researchers also determined that voting machine locks and tamper seals could be easily purchased and used to hide tampering. They also uncovered widely used default passwords and abysmal password management practices imposed by vendors. An unencrypted FTP connection programmed to communicate to a nonexistent domain also drew attention from the researchers. According to the panel, encryption was present in voting machines “only in the marketing materials“.
The talk crystallized the basic fact that even after decades of diligent research and documentation, the overall state of voting machine security in the United States is terrible. They expect to expand their voting machine hacking village at the next DEFCON in Las Vegas, revealing further major shortcomings in the architecture of democracy.
Dark Caracal: How to Burn a Spy Agency and Get Away with It
Cooper Quintin from the Electronic Frontier Foundation covered a complex set of investigations into state-sponsored hacking and espionage, tracing command-and-control servers, malware and more around the world. This talk showed how a team of investigators were able to detect a whole network of electronic espionage particularly targeting Windows and Android users and harvesting their data. Taking advantage of misconfigurations by the perpetrators, they were able to monitor the network’s behavior and its administrators’ activities for three months.
See a Unicorn Riot interview with Quintin from the 2016 LibrePlanet free software conference here.
Unicorn Riot will continue to release further information from this year’s HOPE Conference as capacity permits.
Please consider a tax-deductible donation to help sustain our horizontally-organized, non-profit media organization:



