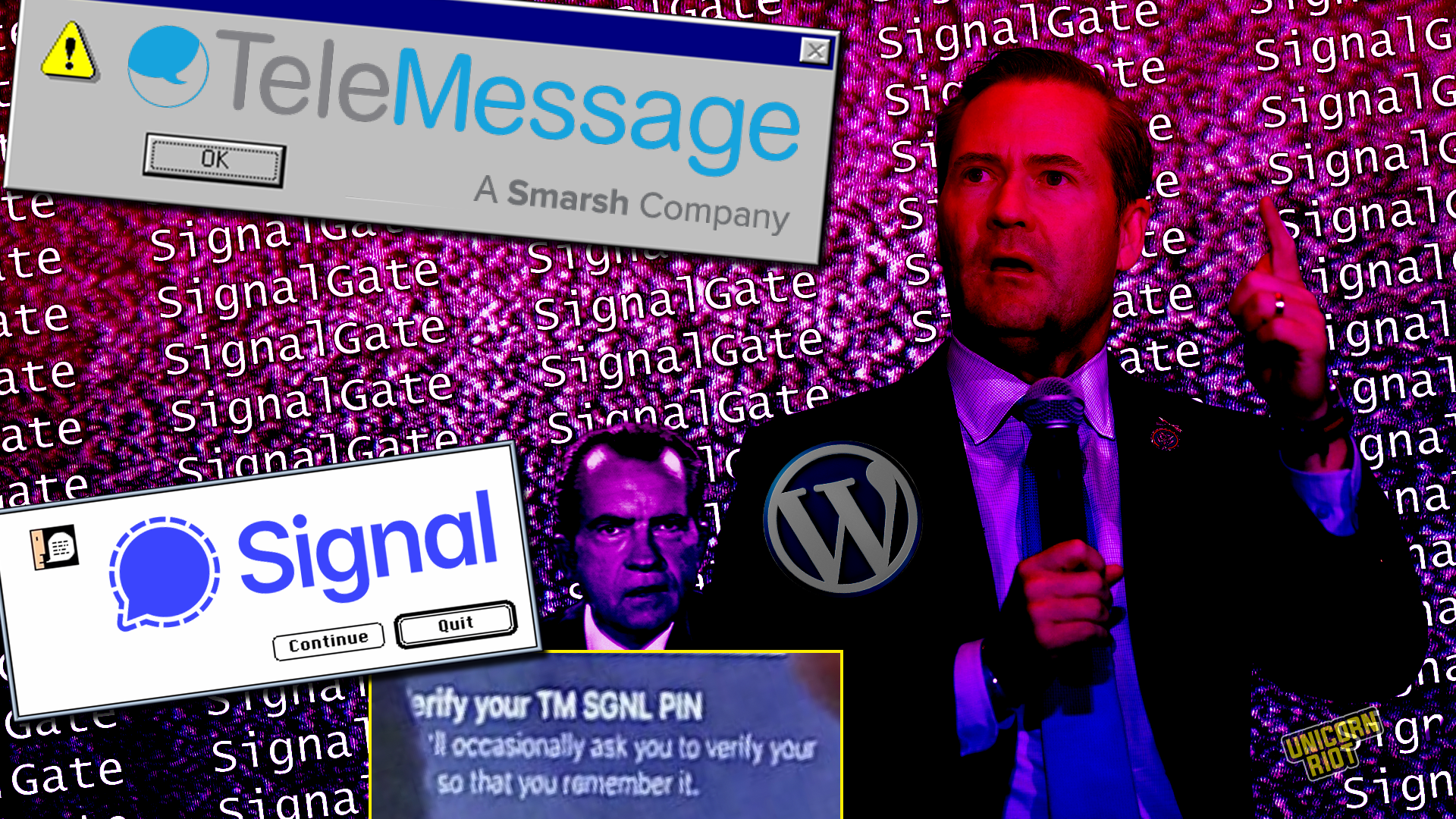
SignalGate Meets WordPress: Outgoing National Security Adviser’s Phone Dumps Messages via Israeli App
National Security Adviser Mike Waltz had a rough Thursday. While he made it in that job longer than Mike Flynn, he’s out after just over 100 days. Unfortunately for him, Reuters press photographer Evelyn Hockstein caught him using a Signal-like interface to view chats on his phone under the Cabinet table at a public meeting. Much like the earlier SignalGate chats, key Trump officials like Vice President JD Vance and Tulsi Gabbard show up in the messages on that sole photo.
Signal users regularly get messages reminding them to enter their PIN number, a kind of secondary lock on the account data. This phrase “TM SGNL” was oddly different than normal on Waltz’s phone, which quickly led people to a software vendor called TeleMessage that is based in Israel, first reported in detail by 404Media. TeleMessage is owned by Portland, Oregon-based Smarsh, which provides communication compliance, recordkeeping, legal, and other software according to its website.
Smarsh started to acquire TeleMessage in 2022 to “deliver unmatched capability for mobile communications compliance for the hybrid workforce.” Official developer docs show that TeleMessage’s “tech stack” has included a user management function implemented on the server side to connect directly with a WordPress site, a few eagle-eyed people pointed out online.
Additionally, Unicorn Riot found that at least one access pattern must have been implemented through the WordPress Gravity Forms plugin, which is a very unusual design choice for a set of company programs with such sensitive devices to track. (Details on that below.)
By Friday evening, NBC News, The New York Times, Wired, Truthout, and TalkingPointsMemo had followed 404Media and DropSiteNews in covering this app. U.S. Senator Ron Wyden (D-Oregon) told the Times, “This is incredibly dumb… The government has no reason to use a counterfeit Signal knockoff that raises obvious counterintelligence concerns.” Technologist Micah Lee analyzed a version of the Android app, then the app source code and git development logs turned up as well.
TeleMessage’s American headquarters is on Lenox Road in Atlanta, while the “Sales and R&D Headquarters” is on Ha-Mefalsim Street in Petah-Tikva, Israel. DropSiteNews found staff and leadership at TeleMessage had experience with the controversial NSO Group spyware maker, IDF technical intelligence and Unit 8200, which is the “cyber warfare” unit that serves as Israel’s National Security Agency equivalent.
The Tel Aviv suburb has other high tech headquarters including Teva Pharmaceuticals, IBM, Oracle and an Intel research center. Last year, Unicorn Riot reported new details about Cobwebs, a controversial Israeli-based social media surveillance company which has contracted with the Department of Homeland Security.
Sections: TeleMessage Markets Signal Archiving • Enter the TeleMessage API … And WordPress Gravity Forms • Hosting Questions and FedRAMP • The WordPress Puzzle: This Seems Absurd • SignalGate and NARA Records Retention
TeleMessage Markets Signal Archiving
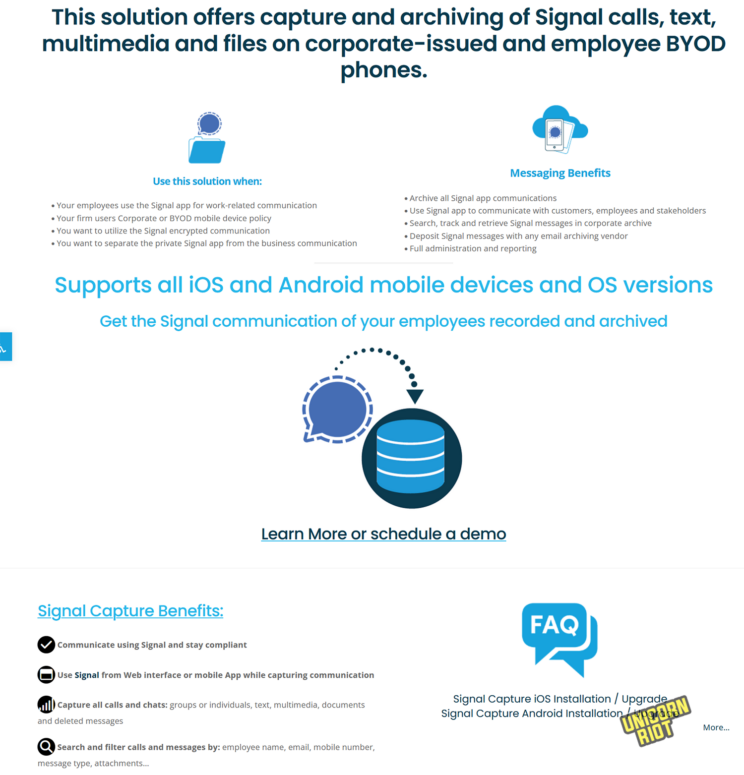
TeleMessage says it can “CAPTURE, ARCHIVE AND MONITOR MOBILE COMMUNICATION: SMS, MMS, Voice Calls, WhatsApp, WeChat, Telegram & Signal,” as well as network carrier capture, voice calls, and Signal capture: “Record and capture Signal calls, texts, multimedia and files on corporate-issued and employee BYOD [bring your own device] phones.”
Tom Padgett from Smarsh told the Times that no information they collect would be sent in any fashion that “could potentially violate our data residency commitments to our customers,” adding, “We do not de-encrypt.”
Interestingly, the service also has some other ways to capture data at the network carrier level as well.
Its features would clone the Signal traffic and archive it:
- Archive Signal communication for iOS and Android devices
- Uses standard Signal interface and encryption
- Works from Mobile App, Signal Desktop
- Use the native Signal interface and encrypted communication with other users
- Captures & records Signal calls, messages, deletions, including text, multimedia, files.
- Archive Signal message text, multimedia, files, and deleted messages
- Signal communication is uploaded to the company enterprise archive [emphasis added]
- Store the employee Signal communication with employee email, and other mobile communication
- Search, find & retrieve Signal communication based on sender, mobile, content, or text
- Complete separation between private and business texts on BYOD devices
- Automatic archiving operates in the background without any user intervention
- End-to-End encryption from the mobile phone through to the corporate archive
- Maintain all Signal app features and functionality as well as the Signal encryption
A couple screenshots of the current version of that marketing site below:
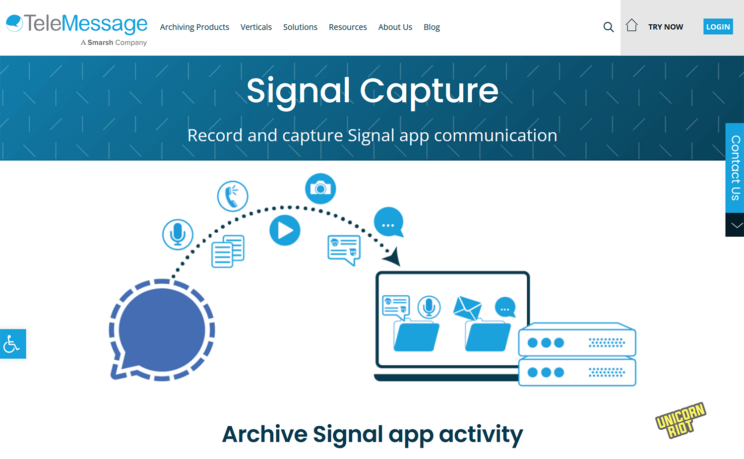
A video published four months ago shows the process. The app itself appears as “TM SGNL” and it’s a fork of Signal — an alternate version which can still message other signal users, but it pushes archive copies of everything sent and received to another server.
Enter the TeleMessage API … And WordPress Gravity Forms
Let’s dive into the technical details here; it’s pretty straightforward. The URLs involved shed important light on the software packages in play. Interestingly, the TeleMessage software has a substantial public API documentation section within which lies at telemessage.com/developer. We don’t know the protocols by which the “TeleMessage SGNL Archiver” or “TM SGNL” would communicate with its archiving server, but we can see what services the vendor made available to access its tech stack, via the official documentation. (Note this is entirely public information below – it wasn’t obtained through any advanced techniques).

API (application program interface) requests, in this case a common industry interface style called a REST API, are a minimalist version of when a browser requests a webpage and a server sends it back — there is a URL pattern to it. So for example https://example.com/rest-api/list-events might return an array of event URLs. (These requests take the form of HTTP request methods or “verbs”, usually POST and GET.)
The upshot here is that there is some kind of interface for feeding data programmatically through this API into the archiving system, and it might not be used with that particular Signal app. However, looking at this API can show us the likely nature of part of this tech stack, which would seem to be connected to at least some White House officials’ phones.
Grizzled WordPress developers know that there is a familiar URL pattern to requests sent into the server from remote machines. That WordPress pattern is present in the TeleMessage API design, and even better, we noticed that the suffix “GF” probably signifies the extremely common webform plugin Gravity Forms, which uses a URL path like /wp-json/gf/v2 — commonly, v2 would mean the second version of the API.
Gravity Forms REST API version 2 has this example code for sending a request into a WordPress site running Gravity Forms, using the common free software tool curl . In this command, developers often use a ‘localhost’ server for testing examples. The URL path behind that shows the main URL in the server for accessing the WordPress JSON Gravity Forms API version 2 “endpoint” URL inside a WordPress website instance ( /wp-json/gf/v2 ) :
curl --data [EXAMPLE_DATA] --header "Content-Type: application/json" https://localhost/wp-json/gf/v2TeleMessage docs show their total API is based, at least partly, on this pattern. The TeleMessage Provision Users function is pretty clearly a Gravity Forms form submission, in fact, it is sending you to form ID #87 on their main corporate website specifically. In the example, www.telemessage.com is the target server URL to send messages to, using the Gravity Forms interface, by sending an HTTP POST message to the following path at the base URI https://www.telemessage.com :
POST /wp-json/gf/v2/forms/87/submissions“Provision Users via TeleMessage service. You can Activate/Delete/Change Details/Suspend a New/Existing User using TeleMessage Provisioning API. First, we need to create the message Body Data with sender authentication details, message content and recipient … and then by using your favorite programmatic language to send this Data to the TeleMessage REST API endpoint”
TeleMessage API documentation featuring a WordPress Gravity Forms specific form ID address.
In the TeleMessage code samples below, The “input_” properties are matched to form fields that would have been defined as Gravity Forms fields on form #87. The first screenshot is a “JSON Payload” format example, while the second is a PHP language implementation that would send a similar payload to the WordPress Gravity Forms API Form #87 endpoint.
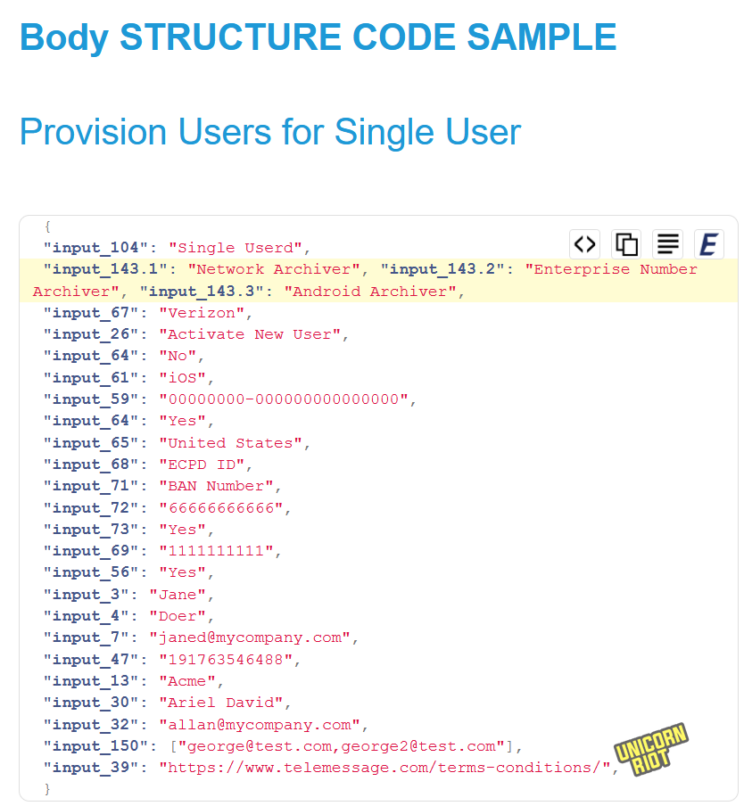
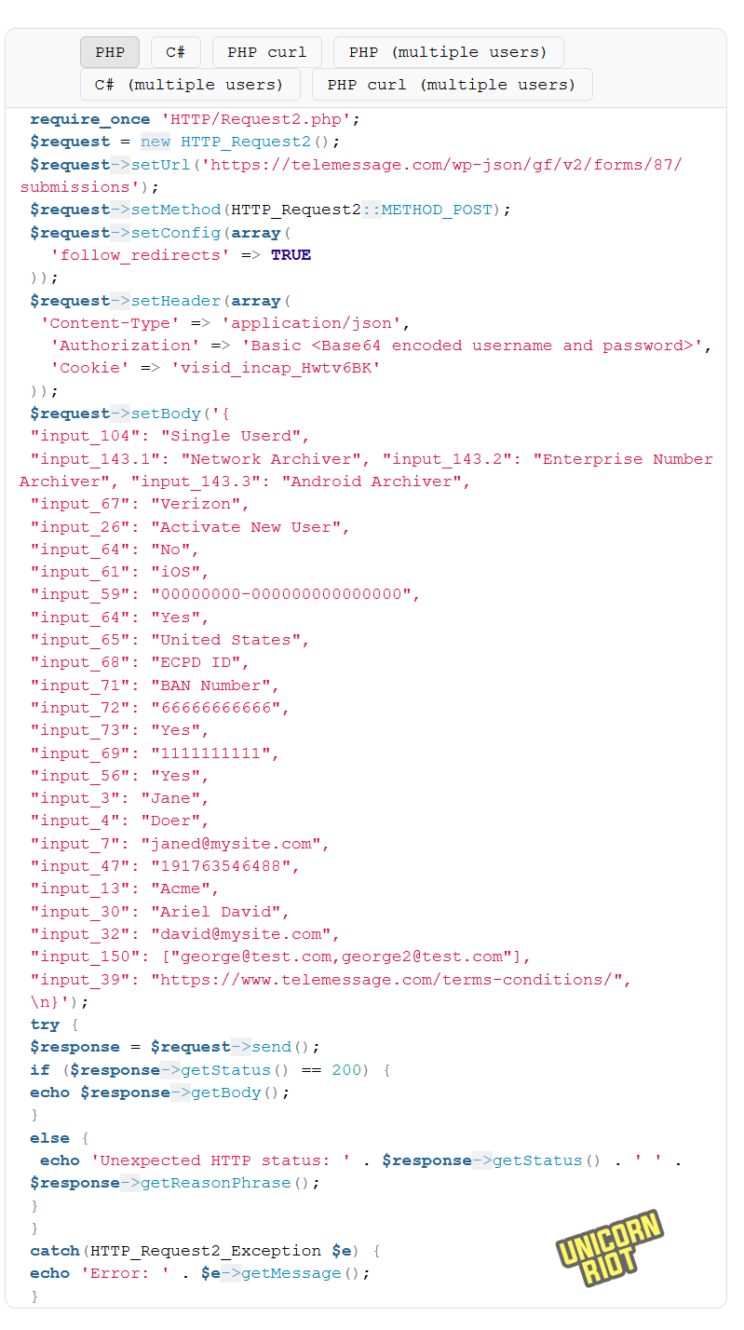
There is also a detailed API for sending messages. There is a REST server described at a different URL with a different server endpoint in the “send a message” documentation. It goes to https://rest.telemessage.com and the URL pattern POST /rest/message/send, which is not a WordPress / Gravity Forms URL pattern.
Additionally there is a Github code repository of a PHP library for talking to the REST interface but it is 10 years old; the Java one is similar. Micah Lee obtained an 87-page user manual published last year with a lot more information.
Hosting Questions and FedRAMP
For US government use, these kind of services would most likely be run to a separate server to run in a government-certified facility, ideally one certified with Federal Risk and Authorization Management Program (FedRAMP) or similar — a program that got new policy rules last summer from the Biden White House.
In short, TeleMessage seems to imply it is a FedRAMP-certified service by acting as a partner to Microsoft:
“As a Microsoft-partnered mobile archiving solution, TeleMessage allows Microsoft 365 compliance centers to import, archive, and monitor for compliance purposes the text messages and calls of regulated employees directly from the instant messaging software used by the organization. Importantly, mobile communication from all the important carriers, including AT&T, FirstNet, Verizon, etc., can be archived directly for compliance. Employers can capture information directly from Android and iPhones, while also having access to communication happening via instant messengers, such as WhatsApp and Signal.
Given that the solution integrates with Microsoft Compliance solutions, including Advanced eDiscovery, Information Governance, and Communication Compliance, federal agencies can have a single repository for their mobile archiving needs. This repository can go a long way in helping the agencies meet Public Records, National Archives and Records Administration (NARA), and Freedom of Information Act (FOIA) requests.”
However, on Friday, Wired reported that TeleMessage is not FedRAMP certified as a service (referring to this directory of vendors).
FedRAMP servers do not necessarily have to be in the United States — there are some in Britain, for example. FedRAMP rules don’t require administrators to be U.S. Citizens either, industry sources say. In a February press release with dual bylines in Tysons Corner, Virginia and Petah Tikva, the Israeli cell phone investigation and break-in tool software provider Cellebrite, congratulated itself for achieving “FedRAMP High ready status” for its Cellebrite Government Cloud platform; details here — it is not yet active. It’s not clear if that server is in Israel or the U.S., but regardless, the company is Israeli-based.
Agencies are not supposed to put “export-controlled items” (e.g. sensitive weapons data) on overseas FedRAMP platforms. Google Cloud Services explains how FedRAMP is divided into Low, Moderate and High impact servers.
The server domain name archive.telemessage.com, which sends out emails shown in the official video above, is currently linked to three IP addresses inside Amazon Web Services network AS14618 in northern Virginia, according to public records. Additionally, the 2020 privacy policy is here; it says that Chinese users must have their records stored in a Telemessage server in China for legal reasons (that PDF is linked from the Apple App Store page for the app). More info about the archive configuration was reported by Micah Lee.
The WordPress Puzzle: This Seems Absurd
“It’s mind-blowing that the federal government is using Israeli tech to route extremely sensitive data for archival purposes,” was how former National Security Hacker “Malware Jake” Williams described this situation to Wired, but the vendor’s design decisions uncovered above are even more baffling.
The idea that a WordPress Gravity Forms interface would be attached to software that needs to collect Signal messages from White House personnel (or really anything highly sensitive) seems a little out there. WordPress is a Content Management System (CMS) primarily designed to generate web pages and similar services like E-Commerce or information portals. (WordPress is free software and anyone can run it – we don’t have any signs of any WordPress-related companies involved with any of this.)
While REST APIs are commonly used in software like WordPress to run huge businesses and government websites, it is not common at all to hear of WordPress (or Gravity Forms) being integrated with telecom devices of top government officials who might be discussing sensitive information.
it is very odd to have a CMS system designed to publish web pages integrated with a platform for collecting telecom messages, which shouldn’t need to access any CMS-generated webpages whatsoever. Gravity Forms, like any piece of software, faces its own security challenges. Just on May 1, the security vulnerability warning CVE-2024-13845 was released.
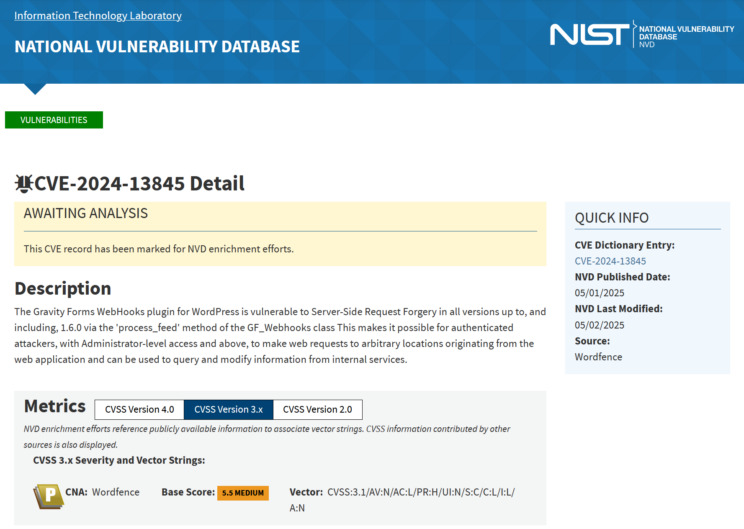
This issue, found in versions below and including 1.6.0 (released in February), allows an attacker to break into the WebHooks plugin, if present, via a Server-Side Request Forgery; if the attackers had administrator level access already, they could make requests to get deeper in the system, retrieve and modify records. There could be other vulnerabilities in this stack, besides any political or management issues that might come with vendors or other actors misusing the nearly priceless data that this app would be collecting and archiving continuously.
Thus, whoever ends up reviewing the vulnerabilities here could have to look at whether the U.S. government was exposed to CVE-2024-13845. As cryptographer Matt Green noted to Wired, “I have no doubt the leadership of the US national security apparatus ran this software through a full information-assurance process to ensure there was no information leakage to foreign nations. Because if they didn’t, we are screwed.”
There may be some risk of intelligence collection by foreign intelligence whenever any software integration and messaging is added, even if locked behind secured servers. Israel’s telecom industry has been tightly integrated with the U.S. market and law enforcement for decades, including other sensitive technologies like wiretap or “trap and trace” devices.
Even if foreign telecom vendors act in good faith to protect the political contents with which their systems are connected, they themselves can get hacked by other actors. MalwareJake said to Wired, “Even if TeleMessage isn’t willingly giving it up, they have just become one of the biggest nation-state targets out there.” Since the 1994 rollout of the Communication Assistance for Law Enforcement Act (CALEA), there have been other controversies with Israeli contractors in the federal telecom wiretapping space.
SignalGate and NARA Records Retention
This spring’s SignalGate scandal appeared to show that disappearing messages were active, which is a potentially illegal configuration of these phone devices — the records of government officials are in the public trust and are supposed to be collected by the National Archives and Records Administration (NARA). The liberal group American Oversight is suing over this issue and sought emergency court order injunctions in April.

Over the decades many officials have tried to duck these laws and rules by trashing documents — many were famously shredded by Oliver North when Iran-Contra unraveled in 1986-87. North didn’t realize his cutting-edge IBM email system “PROFS Notes” had an administrator backup system, revealing items to the Tower Commission investigators he and his colleagues thought they’d already nuked.
The most famous example of White House records management involved Richard Nixon’s recordings around the Watergate scandal, but Kennedy and Johnson also taped a lot of their activities.

So, in the aftermath of Signalgate, TeleMessage might be helping the White House comply with its NARA recordkeeping obligations, but they are using a foreign company’s software to do so, even though the corporate parent company is based in Portland, Oregon and if Wired is correct, this software is not a FedRAMP certified vendor. Within this stack, at some point, the company documented an API for specific WordPress Gravity Forms form, which was designed to manage the users on the system.
Signalgate appears to have cost Waltz his job; he’ll get punted to the UN Ambassador role in New York after an embarassing confirmation hearing, most likely. Marco Rubio is taking on another role in this mix as Waltz is removed. Rubio will be Secretary of State, National Security Adviser and oddly, acting Archivist of the United States, which is the lead official at NARA responsible for gathering all these records.
NARA was involved with the federal prosecution of Trump in Florida over the sensitive and classified records he stashed in Mar-a-Lago — a case that was handled slowly by Florida U.S. District Court Judge Aileen Cannon and dismissed last July. It seems the president is keeping the archivist job close to the inner circle, lest his recordkeeping management practices get him indicted yet again someday.
Cover image composition by Dan Feidt. Mike Waltz photo via Gage Skidmore. TM SGNL PIN excerpt via Reuters/Evelyn Hockstein TPX Images of the Day / 404 Media. Nixon via Thomas Hawk.
Follow us on X (aka Twitter), Facebook, YouTube, Vimeo, Instagram, Mastodon, Threads, BlueSky and Patreon.
Please consider a tax-deductible donation to help sustain our horizontally-organized, non-profit media organization: