Hacking Drones at DEFCON: “All Skyz Belong To Us”
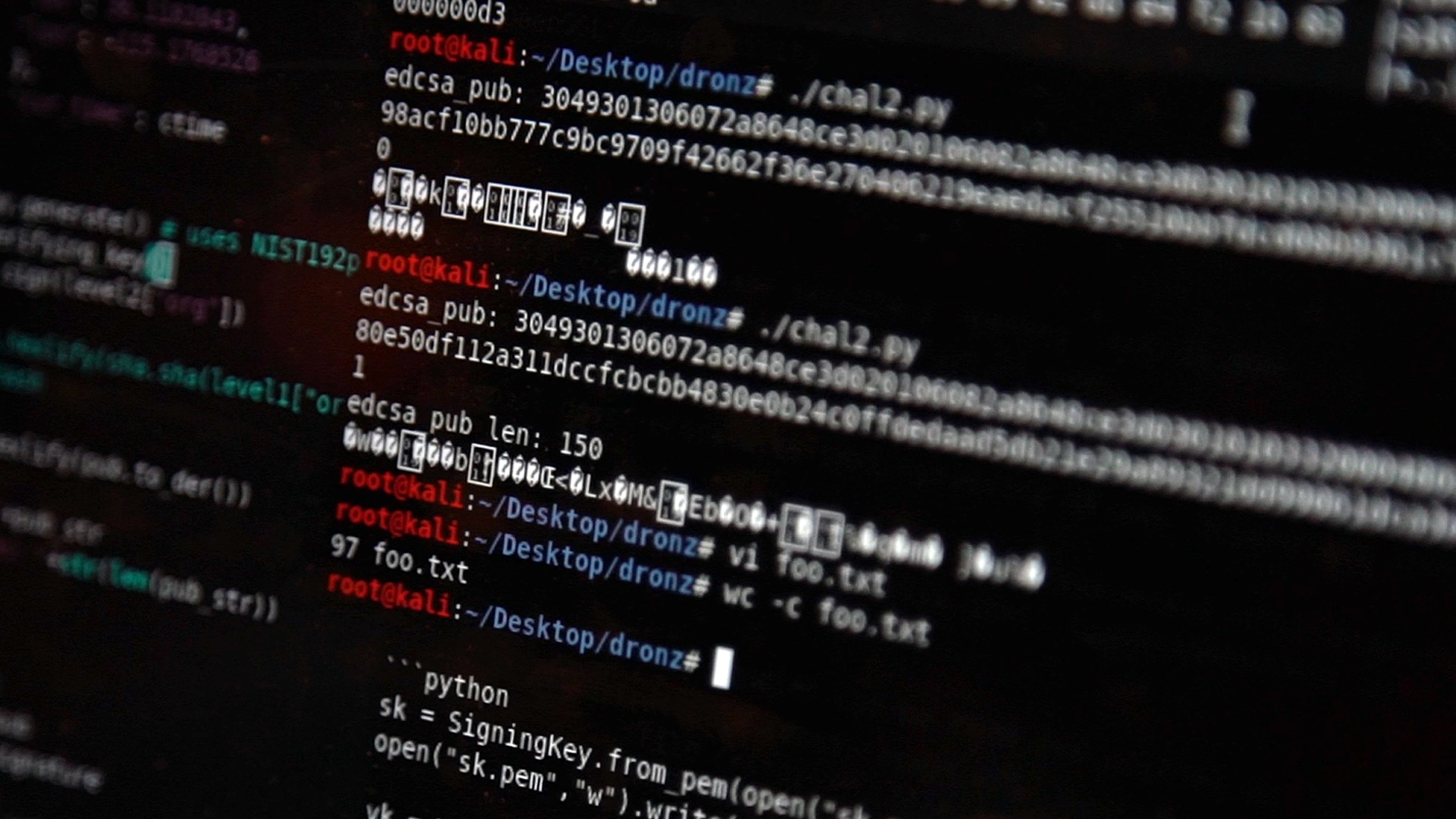
Las Vegas, NV – This years DEFCON hacking conference featured a new village called “DroneWarz”, which focused on the research and development of offensive and defensive drone technologies. The Drone Hacking Village (DroneWarz) offered multiple hacking challenges, including more than twelve skill-based drone hacking challenges…