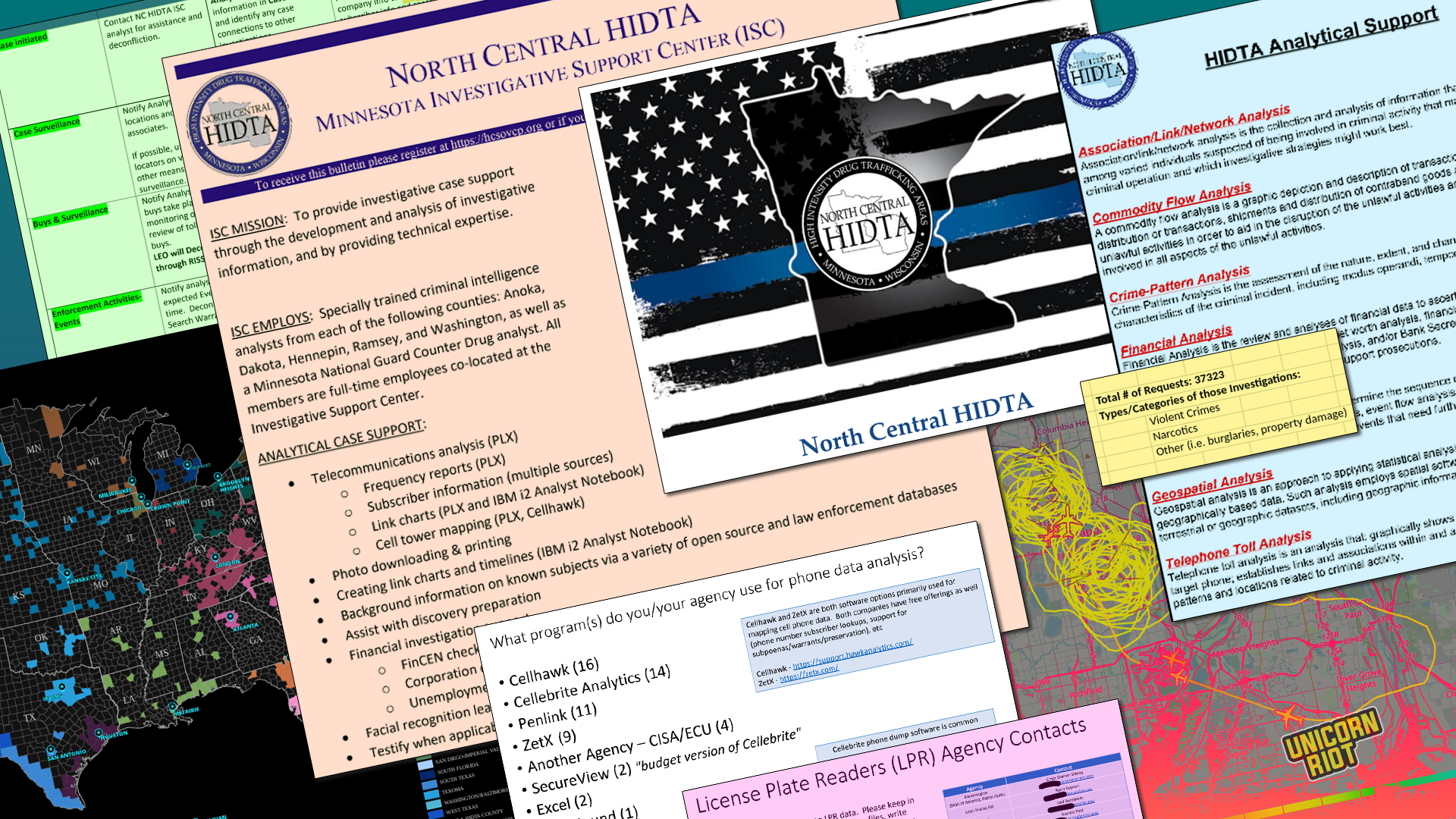
Criminal Intel Files Show Facial Recognition, Warrantless Surveillance in Minnesota
A little-known multi-agency drug war group runs thousands of facial recognition scans and other surveillance operations. We found over 37,000 requests for support, connecting at least 233 law enforcement organizations in Minnesota and beyond.
Minneapolis, MN – Documents obtained via a series of public records requests from the Hennepin County Sheriff’s Office (HCSO) provide rare insight into police intelligence gathering. The documents include case numbers in which facial recognition was used, details about systems that gain access to vehicle entertainment systems, geospatial intelligence, cell phone snooping and more.
Many drug and other task forces as well as more routine law enforcement operations within the region receive intelligence from investigators within the Criminal Intelligence Division (CID) and Criminal Information Sharing and Analysis (CISA) units. Within this division is the High Intensity Drug Trafficking Areas Investigative Support Center (HIDTA ISC). Amid these units the Real Time Analysis Center (RTAC) is a hub for tactical operations planning.
The Hennepin County Sheriff’s Office leases office space in downtown Minneapolis where HIDTA and CISA units work side by side, serving as a clearinghouse and command center both supporting criminal intelligence gathering as well as real time field operations.
Homeland Security equates these operations with fusion centers. This multi-agency investigative effort combines various intelligence pipelines from hundreds of police and other sources and is bolstered by data mining and state-of-the-art surveillance technology.
HIDTA operations, like the North Central HIDTA, exist across the United States with little public scrutiny. Locally, the conversation around police use of facial recognition largely features police officials explaining that it’s a powerful tool they only use for the most pressing investigations. Now, the dataset Unicorn Riot is making public shows over 1,600 facial recognition searches in 1,395 days for investigations including “property crimes,” and other arguably lesser offenses.
This report covers a range of technologies used by criminal intelligence analysts and investigators within the County-maintained facility that’s used as part of a multitude of police operations across the region. The legal threshold to perform cellphone surveillance in particular, but also regularly run facial recognition and other invasive technologies, are clearly lacking as is shown by the documentation obtained. The federal HIDTA program enables this data-driven approach to policing alongside the County’s criminal intelligence units, pooling access to resources, data and analysis.
Note: the files featured here are all available in the Resources section at the end. Use our new tabs to peruse HIDTA-related files.
Sections: The Police Web – 37,000 Requests – Facial Recognition – Berla: Data Mining Automobiles – Operations and Tactical Planning – License Plate Readers – Cell Phone Data – Cellebrite and Phone Extraction – Minimal Oversight – Resources
The Police Web: CID, CISA, HIDTA ISC, Etc.
The log of facial recognition searches spans roughly 1,300 days from January of 2019 to late October 2022. The log indicates investigators ran 1,677 facial recognition searches since Jan. 2019.
Of those searches, 921, or 54%, were not associated with any case numbers. It’s therefore unclear from the data if those particular searches were in furtherance of legitimate law enforcement functions.
HCSO’s website says the Criminal Intelligence Division (CID) provides “timely and accurate analysis of criminal information to area law enforcement. The division analyzes information to identify crime patterns, forecast criminal trends, generate investigative leads, assist with identification and apprehension of suspects involved in criminal activity” and provide threat information.

Any group with “Intelligence” in their name will naturally include a litany of acronyms – bear with us.
“CID contains many units that support criminal intelligence and crime analysis, including the Criminal Information Sharing and Analysis (CISA) Unit, North Central High Intensity Drug Trafficking Areas (HIDTA) Minnesota Investigative Support Center (ISC), Hennepin County SHIELD public/private sector partnership program, and more.”
Hennepin County Sheriff’s Office – CID About Page
Another briefing document explains that “The ISC initiative is led by the Hennepin County Sheriff’s Office.” Furthermore, the ISC supports investigations into violent and drug crimes and also “financial” and “other major crime investigations.” The County explained that the “other crimes” set includes offenses such as burglary and property crimes. See the background video HCSO released for more.

The High Intensity Drug Trafficking Areas (HIDTA) program was created by an act of Congress in 1988 during the Reagan-era expansion and federalization of the War on Drugs. HIDTA assists “law enforcement agencies operating in areas determined to be critical drug-trafficking regions of the United States.”
HIDTAs exist in all 50 states and US territories, wielding a vast array of surveillance tools and operations including over 1,500 DEA special agents. HIDTA task forces include federal, state, county and local law enforcement officials. These efforts are assisted by electronic surveillance, license plate readers, data-brokers, aerial surveillance, confidential informants, cellphone analytics, social media intelligence, and more.
In 2021 the HIDTA annual budget was $290 million and “President Biden’s FY 2023 budget calls for a historic $293.5 million in funding for the HIDTA program,” according to Whitehouse.gov. Overall, the Drug Enforcement Agency’s (DEA) ever-expanding budget now exceeds $3 billion. Tax dollars are not the only revenue stream for the DEA who seize property and currency to the tune of hundreds of millions of dollars a year via asset forfeiture.
Learn more about Homeland Security asset forfeiture via our leaked ICE-HSI manual in #Icebreaker Part 2.
In addition to federal agents, the local HIDTA program – North Central HIDTA – employs “specially trained criminal intelligence analysts” from “Anoka, Dakota, Hennepin, Ramsey and Washington” counties and a “Minnesota National Guard Counter Drug analyst” according to the documents.
2020: Plane Seized As Part of Counter Drug Asset Forfeiture Mission Used to Resupply Police with Riot Munitions During George Floyd Uprising
37,000 support requests keep HIDTA – ISC busy
Via data practices requests, Unicorn Riot found that ISC provided support for over 37,000 requests from law enforcement partners.
Unicorn Riot obtained data detailing the names of law enforcement organizations that requested investigative support from the ISC; the dates and types of cases in which the center provided real time support through the RTAC; spreadsheets logging facial recognition searches with attached case numbers, and more records.
Violent crimes and narcotics investigations were bolstered by the group, along with a vague category labeled as “Other” which included burglaries and property damage. These requests from other law enforcement organizations for some kind of support from the ISC totalled 37,323 according to Hennepin County logs. While no date range was given for that number, it shows the dependency investigators across Minnesota (and beyond) have on surveillance and analysis by the ISC.

These operations run more or less around the clock, processing and poring over scraped data of all kinds. There doesn’t appear to be a type of digital information which criminal intelligence operatives lack access to – they also routinely receive information from Customs and Border Protection (CBP) and other federal partners.


A Look Behind The Curtain – Facial Recognition in Minnesota
Before UR obtained these documents, an in-depth understanding of how local authorities have used facial recognition was not available. But now, with thousands of cases to observe, it’s possible to illustrate the extent of the technology’s use by regional law enforcement.
Facial recognition is heavily used by CISA/HIDTA investigators for “lead generation.” Finding possible suspects by comparing images and running queries against drivers license databases, or jail booking photos, for example, is one such method of lead generation. Facial recognition is commonly used in conjunction with images posted on social media. These documents also show that a majority of the searches since 2019 did not have case numbers associated, which paints a picture of open and unregulated use of facial recognition.
“Face recognition surveillance presents an unprecedented threat to our privacy and civil liberties. It gives governments, companies, and individuals the power to spy on us wherever we go — tracking our faces at protests, political rallies, places of worship, and more.”
American Civil Liberties Union
Lacking any data to verify a legitimate justification for nearly 1000 searches in around 1300 days shows a lack of transparency and accountability within these programs. It also displays a clear pattern of frequent reliance on a technology that can be both invasive and misleading – especially for communities of color. Automating surveillance amplifies biases and rapid adoption of these technologies has occurred behind closed doors devoid of adequate public oversight.
On Feb. 12, 2021, Minneapolis banned its police department from using facial recognition for surveillance, but that didn’t stop the law enforcement agency from using the controversial technology. The ban’s passage was delayed due to Mayor Jacob Frey’s failure to sign the bill itself, meaning it took five days (excluding Sunday) for the ban to become law following council passage the previous Friday. In effect the ban became law on Feb. 18.
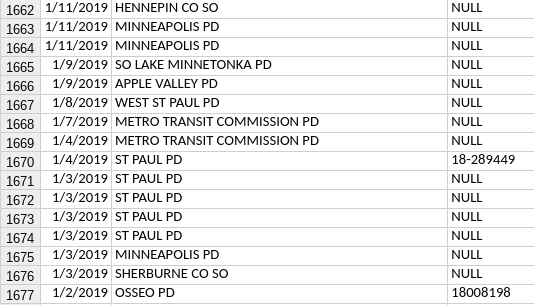
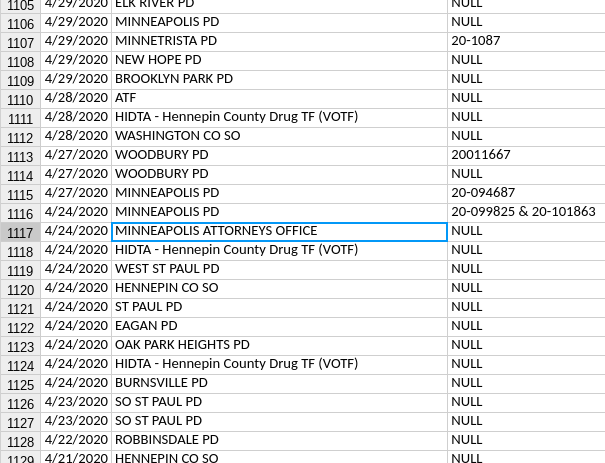
Records show that four days after City Council passed the ban, the Minneapolis Police Department (MPD) requested a facial recognition search and listed the reason as “null.” The request’s justification being listed as “null” prevents the public from knowing any information about the search other than that MPD requested it be performed.
The department requested a similar search 11 days post-ban. According to Minneapolis officials, the search ran nearly two weeks after the ban was passed. This request was in support of a homicide investigation.
The Minneapolis City Attorney’s Office shows up with 16 facial recognition searches in the logs as well. Data requests for specifics about those and other cases are pending and will be examined in future reports. After inquiring about several other requests, Minneapolis explained that one of the cases was, “child neglect/endangerment (inactive),” and another, “theft, case closed.”
State law does not forbid facial recognition surveillance, and in some cases, MPD appears to have circumvented the local ban by outsourcing requests to other agencies. This could potentially shield MPD from liability over those searches, as one city cannot regulate another city’s police force. A joint Minneapolis and external agency search occurred as recently as Sept. 2022. The facial recognition ban does not stop the MPD from “complying with the National Child Search Assistance Act… or other federal statutes requiring cooperation in the search for missing or exploited children.”
Civil rights advocates in Minnesota foresaw this problem. Munira Mohamed of the ACLU of Minnesota, who advocated for the banning of police facial recognition in Minneapolis, asked, “If you pass a local law curtailing police abuse, how do you know they can’t skirt around that with the help of another agency?” Mohamed also said, “we need to halt the use of these surveillance technologies until there are meaningful laws and oversight that can regulate it and protect everyone’s constitutional rights.”
Law enforcement throughout the state requested facial recognition searches. Police in Robbinsdale, an adjacent suburb to Minneapolis, requested over two dozen facial recognition searches since 2019 and most don’t have case numbers attached.
The University of Minnesota Police Department (UMPD) also requests these searches and works with the MPD submitting requests that would otherwise not be legal. The UMPD has requested at least seven searches since the start of 2019.
The FBI, DEA and many federal task forces appear in the logs numerous times. Some other examples from the data – Since Jan. of 2019, the Brooklyn Center Police Department requested these searches 33 times; Edina, 69 times; Champlin 7; Bloomington 42; Elk River 14; Richfield 23; St. Louis Park 30; Metro Transit Police Department 42; and Zumbrota 1. “Other Agency” is listed 24 times.
Berla: Deep Data Mining on Automobiles in Minnesota
In late 2021, investigators started a new form of data mining using a vehicle forensics software called Berla. The surveillance tool, “breaks into a vehicle’s data systems to find, organize and analyze a vast range of information that often includes far more than what the car generates itself,” according to CyberScoop. Data generated by the vehicle, including GPS and other revealing information such as when doors were opened and closed, can reportedly be exploited by Berla.
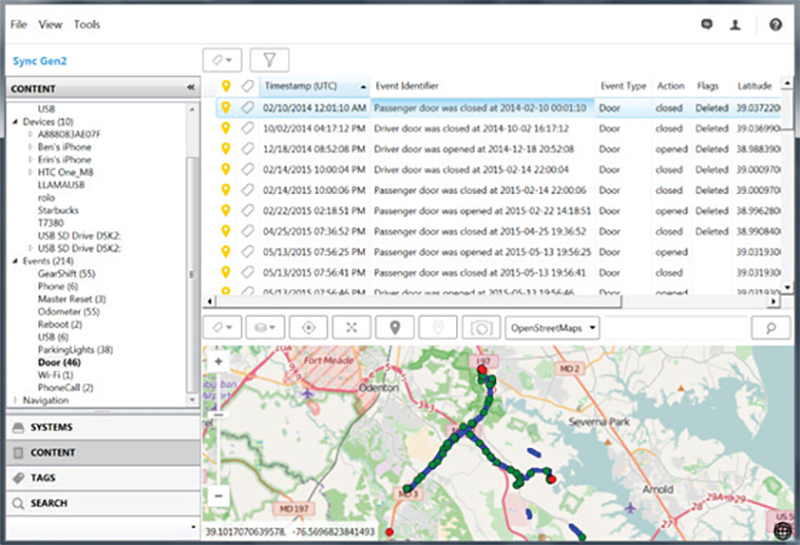
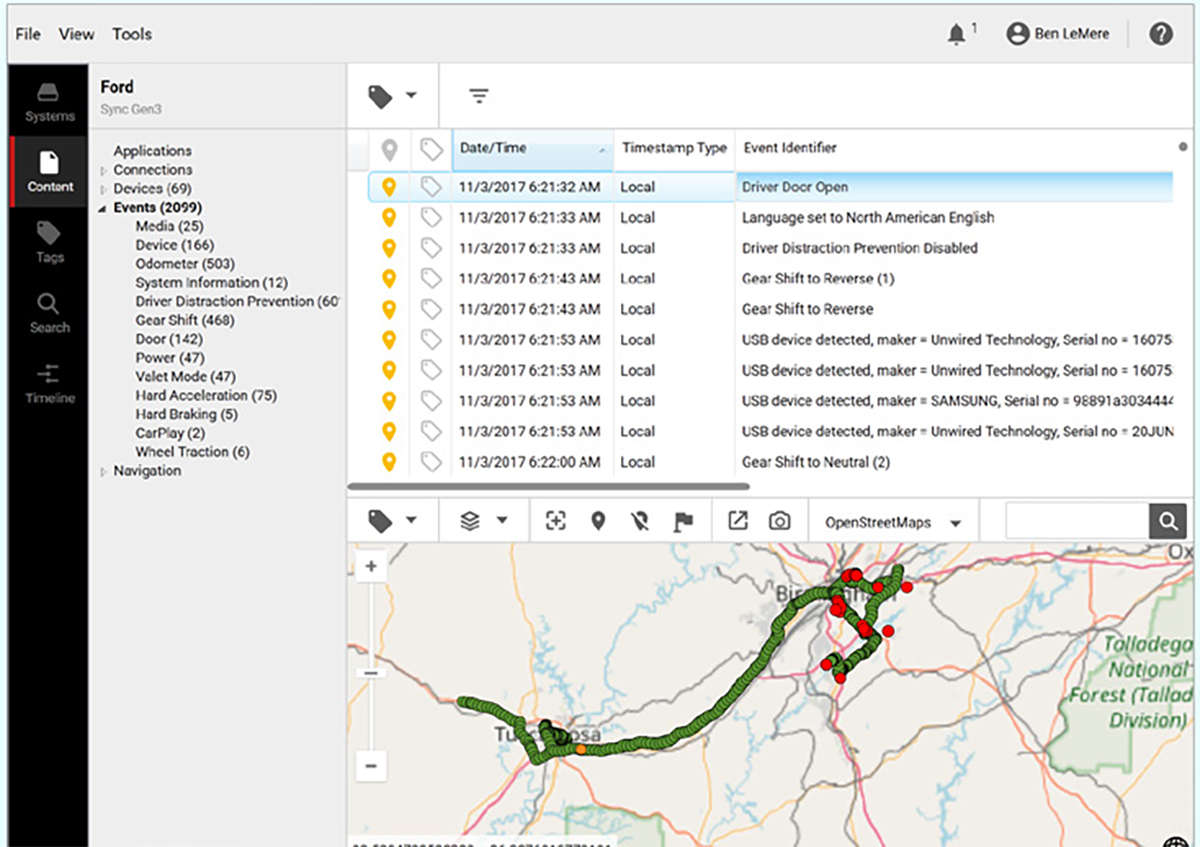
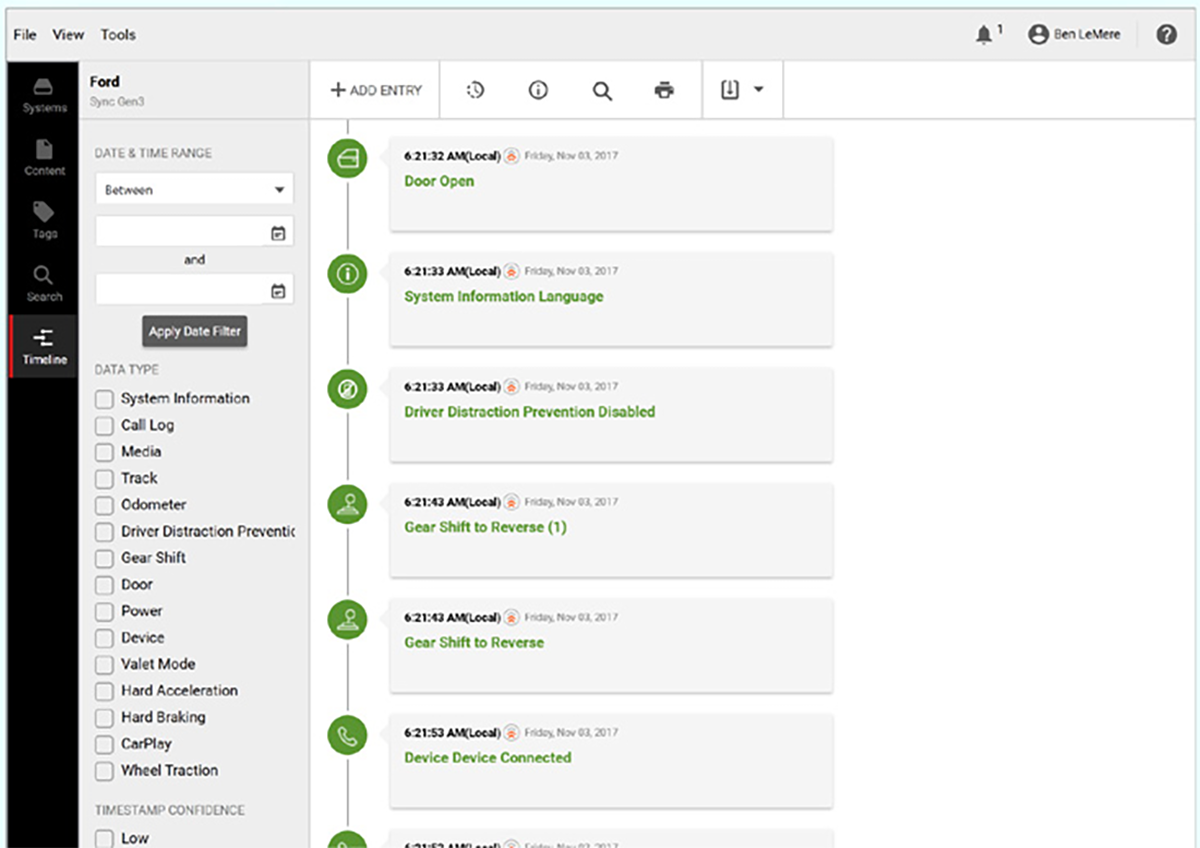
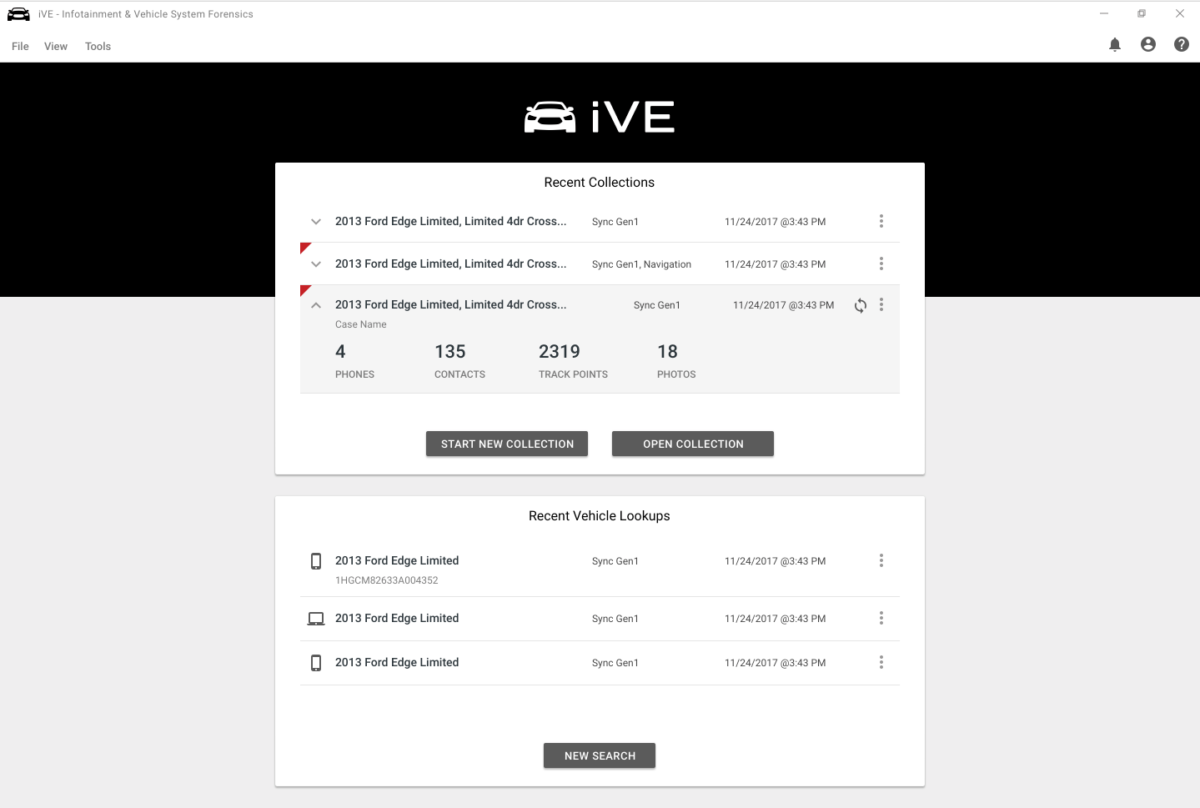
Berla also leverages information stored within vehicles from cellphones and other devices that had connected to the vehicle at one point in time, such as Bluetooth phone connections.
Unicorn Riot discovered Hennepin County records show 33 Berla usages since August of 2021 in furtherance of violent crimes, narcotics and unspecified other investigations, including burglaries or property crimes. The images included above were extracted from Berla promotional materials.
Operations and Tactical Planning: The Real Time Analysis Center
One of the “desks” used during live operations is the RTAC (Real Time Analysis Center) which is critical to “Emergent Event Operations and Tactical Support,” as stated in a HIDTA briefing document. RTAC functions as a command hub for “operational and tactical planning” using large monitors, communications networks and the other systems the ISC can access.
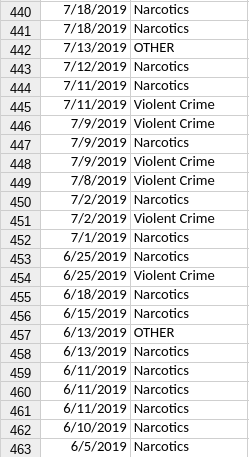
The dataset reveals RTAC was used in support of 462 law enforcement operations from June 5, 2019 to Oct. 26, 2022. The primary type of operation supported by RTAC during that time frame was “narcotics,” which was cited a total of 264 times. The data also show RTAC was used 177 times in “violent crimes” investigations, and again in 21 cases labeled as “other.”

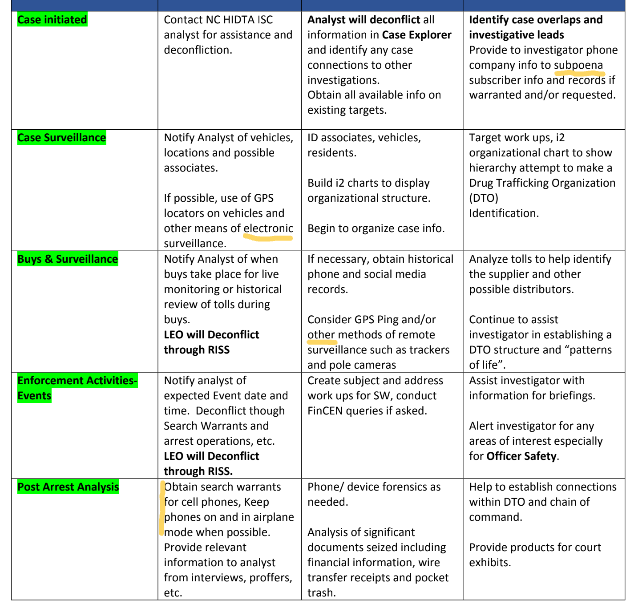
License Plate Readers Data Sharing
A presentation put together for a Minnesota Association of Criminal Intelligence Analysts (MACIA) conference explained, “Please keep in mind that many [agencies] have to pull case files, write reports, or otherwise document every LPR search they do, so please limit requests to cases where all the other vehicle search sources will not get you what you need. Also this should be obvious but requests must be related to an active criminal investigation.”
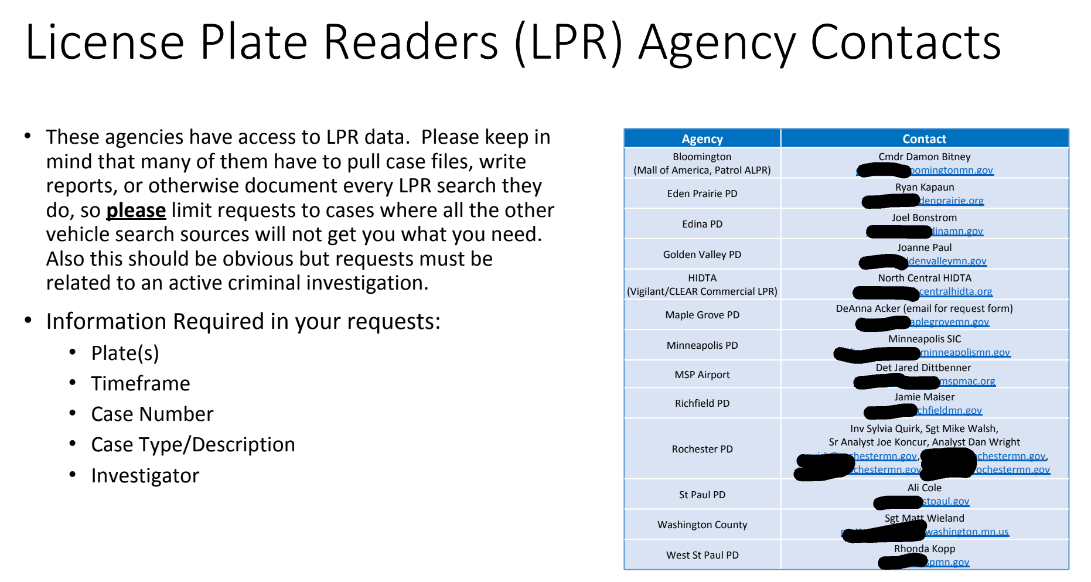
The presentation slide includes a table of point people to contact for license plate reader queries and reveals that HIDTA uses multiple LPR vendors including Vigilant and CLEAR. Vigilant sells, “a nation-wide database of license plate reader data via a secure web-based application and allow intelligence agents to analyze the movement of targeted vehicles as they travel on the nation’s highways,” according to DHS documents obtained by Vice.
Cell Phone Data
Another prime component to these intelligence operations is the analysis of vast swaths of data collected by this constellation of surveillance systems. Call Detail Records (CDRs) reveal a large amount of information about the people using the phone being analyzed – not just who is being called, when and for how long, but also how entire networks of people operate.
One document released as part of this investigation describes establishing “patterns of life,” a common term from War on Terror-era drone assassination campaigns. Using tools and systems like CellHawk and IBM’s Analyst Notebook, agencies piece together digital breadcrumbs, perform link-analysis and pick apart other surreptitiously obtained data.
More about Analyst Notebook: – 2016 interview with Chris Soghoian, Denver police use NSA-grade software, and in anti-terrorism task force job description
Officers need not physically possess the phones being surveilled as cell carriers turn over highly detailed call logs, GPS and other data without any warrant thanks to a little known section of federal code. 28 CFR Part 23 permits law enforcement in the United States to hoover up incredibly sensitive information from Americans under the very low bar of “reasonable suspicion,” despite the Fourth Amendment requirement that searches be backed by probable cause.
More on the problematic policies that govern this type of surveillance on both the local and federal level, and Hennepin County’s convoluted definition of reasonable suspicion from this reporter can be found in the report on Cellhawk, police surveillance of cell phones, and county-level ‘reasonable suspicion’ policies for The Intercept in 2020. The county has a Cellhawk subscription capable of storing over 250,000 call detail records.
Cellebrite and Phone Extraction Tools
Tools to extract data from phones already seized by police perform functions similar to surveillance occurring “in the field” and also provide a trove of potential evidence. Cellebrite is one such forensic extraction device and investigators are instructed to “keep the phone on and in airplane mode when possible,” according to documents obtained during this investigation. Oftentimes, according to the documents, Cellebrite or another extraction device will scoop the data from phones and analysts then use other programs to visualize and otherwise make sense of the information.

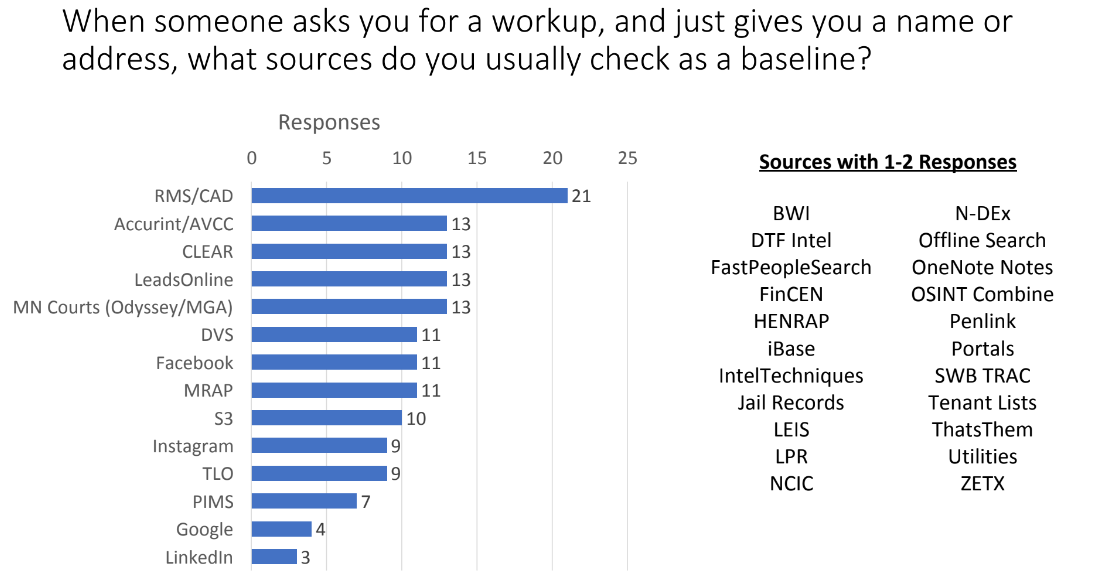
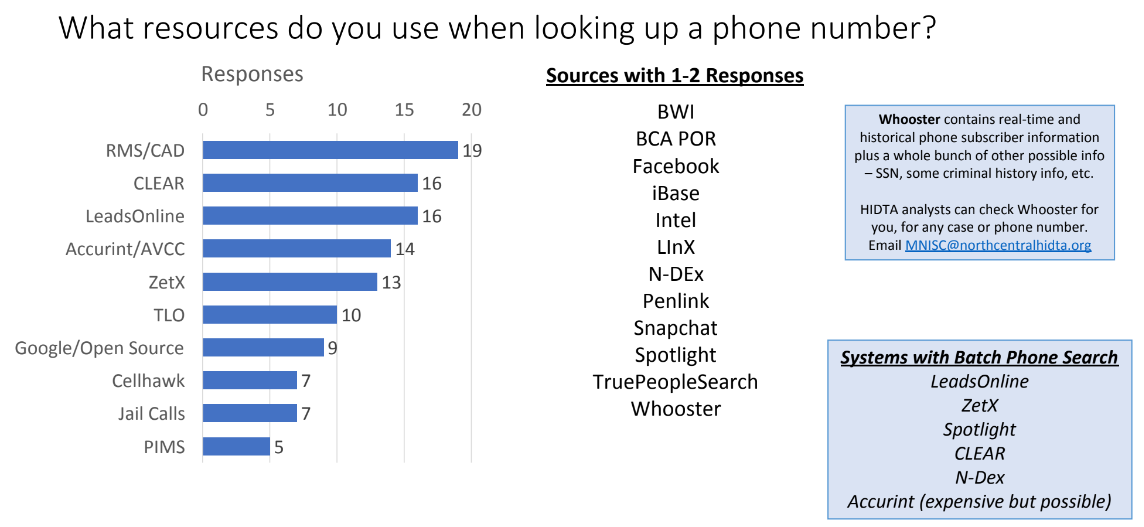
Surveys from a criminal intelligence analyst conference obtained by Unicorn Riot show which products police in Minnesota use to spy on cell phones and collate their data. Giant data brokers like CLEAR and LexisNexis offer an array of products.
One popular system is Accurint, which is marketed by the company as, “cutting-edge investigative technology that can expedite the identification of people and their assets, addresses, relatives and business associates by providing instant access to a comprehensive database of public records that would ordinarily take days to collect.” A summary of the “Hawk Toolkit” from Cellhawk also turned up.
With massive and growing police budgets, the market for domestic surveillance tech grows every year.

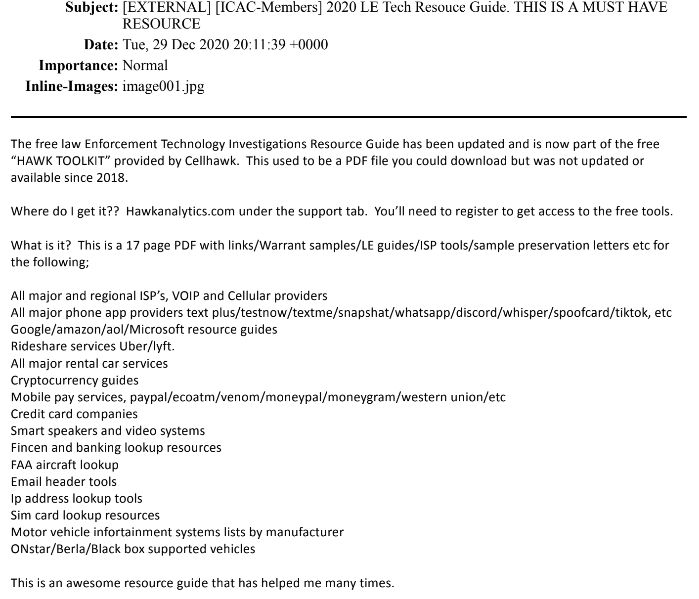
Criminal intelligence analysts fuse information from dozens of partner agencies including Customs and Border Protection. Intelligence networks provide information and assets belonging to federal agencies are routinely deployed in furtherance of domestic policing – including spy tech, aircraft and more.
Increasing Reliance on Aerial Surveillance
Since there are many drug, gang and other task forces running operations at any given time, aerial surveillance has become much more common in the Twin Cities in the last several years.
As recently as November and December of this year, Minneapolis residents could look up and see ‘DAGGER04,’ a Wisconsin National Guard RC-26 circling parts of the city for hours at a time. The last time a C-26 flew surveillance over the Twin Cities was during the beginning of the unrest following the murder of George Floyd.
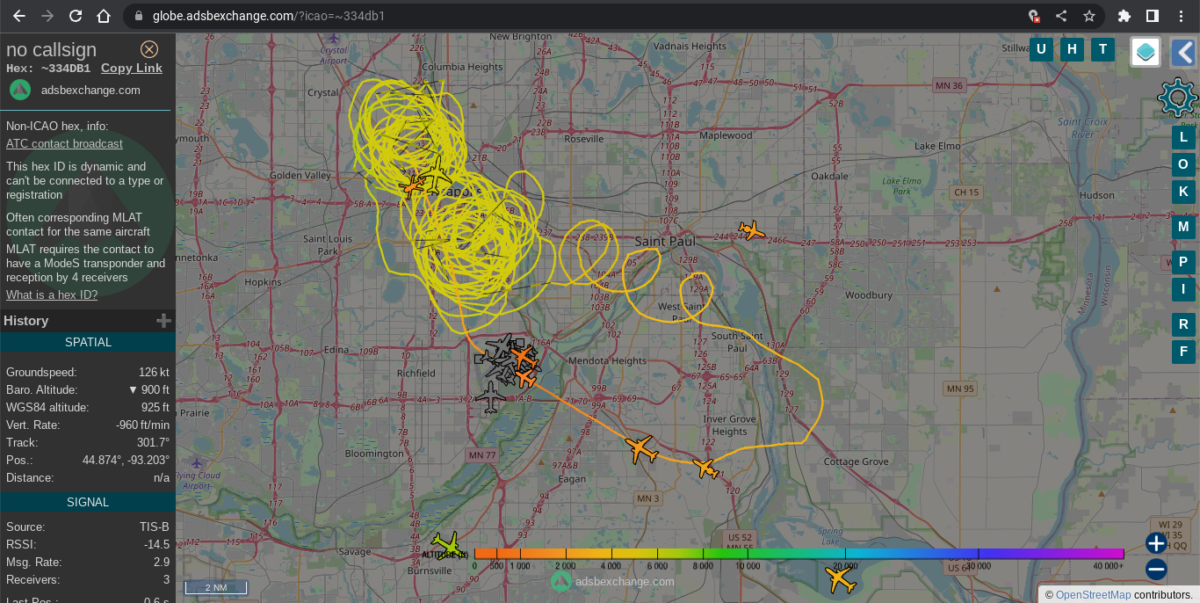
Wisconsin is a member of North Central HIDTA and therefore National Guard assets from the region are available for operations. DEA, FBI, DHS/CBP, and State Patrol spy planes and helicopters are also spotted circling or revealed through Air Traffic Control transmissions on an increasing basis.

Widespread Operations, Minimal Oversight
North Central HIDTA ISC and CISA are rarely, if ever, mentioned by news reporters or elected officials. The consequences of a highly capable, intricately networked group with routine access to some of the most powerful surveillance tools in history is a source of fundamental concern given the lack of oversight. Private cellphone and other incredibly revealing data is obtained without warrants and investigators are using facial recognition on a daily basis.
The intelligence created by these groups is valuable to investigations across multiple states yet the recordkeeping is lacking. Over half of the facial recognition searches since 2019 were listed as “null.” Furthermore, Minneapolis specifically is violating the spirit of one of the only reforms – a ban on facial recognition –of the infamous police department following their murder of George Floyd.
More Resources
Researchers, reporters, anyone interested in exploring the data find the files below. Please give appropriate credits/citations:
- Case Support Records 1: Overall support to LEOs (XSLX, 17KB)
- Case Support Records 2: RTAC real time / exigent event support dates (XSLX, 16KB)
- Facial Recognition Search Log with Case Numbers (XSLX, 50KB)
Sam Richards is an investigative reporter focusing on surveillance, protests and more. Find him on Twitter as @MinneapoliSam. Cover composition by Dan Feidt for Unicorn Riot.
Follow us on X (aka Twitter), Facebook, YouTube, Vimeo, Instagram, Mastodon, Threads, BlueSky and Patreon.
Please consider a tax-deductible donation to help sustain our horizontally-organized, non-profit media organization: