Icebreaker Pt 7 – ICE Case Management Handbook Based on Federal Law Enforcement “System of Systems”
United States – Unicorn Riot obtained confidential Immigration & Customs Enforcement (ICE) policy manuals in 2017. Icebreaker Part 7 covers ICE’s “Case Management Handbook” which was in effect between 2008 and 2016. The handbook is closely based on a critical database structure called the Treasury Enforcement Communications System (TECS), which has been a backbone of federal law enforcement data management and intelligence gathering since 1987.
According to a release by GovernmentAttic.org this 2008-vintage manual was still active policy at the end of 2016. The overall document is 61 pages including the cover. Download the PDF directly here.
Notes on the Case Management PDF are below this story, which covers the context of TECS and the design of its latest surveillance and data gathering replacements.
ice-case-management-handbook-cleanIn recent years the version of TECS referenced in the handbook has been replaced with “Integrated Case Management” (ICM), which is designed and managed by controversial data mining intelligence contractor Palantir, itself owned and controlled by Silicon Valley billionaire Peter Thiel.
In Icebreaker Part 6, Unicorn Riot covered how paramilitary-style Special Response Teams (SRTs) could use TECS to research possible subjects of armed raids. Icebreaker Part 3 covered how cases including fugitives used tracking provided by TECS.
ICE was created by merging several pre-existing government agencies a couple years after 9/11. This manual was written before Homeland Security Investigations (HSI) became a independent agency within ICE, and is instead referred to as “Office of Investigations” (OI) in the manual.
Aside from the information garnered from surveillance and informants, a number of instructions in the handbook cover key information related to court proceedings and discovery for defense attorneys, as well as how certain info about informants should not be placed in the main case files.
Dossier and tracking databases designed by U.S. corporations have been a key instrument of social control for the U.S. government since at least the colonial occupation of the Philippines. As Prof. Alfred McCoy documents in “Policing America’s Empire” and in related lectures, the combination of recently-invented fingerprints and personal dossiers enabled colonial administrators to exercise tight control over the island nation and begin developing US-America’s unique forms of counterinsurgency to prevent the overthrowing of the colonial power structure.
American companies such as IBM assisted Nazi Germany’s government in tabulating and tracking targeted minorities including Jewish and Roma people for detention and eventual extermination in the European Holocaust. IBM and Polaroid assisted the apartheid-era government of South Africa which relied on American companies’ services to implement sophisticated identity-tracking measures in uphold racist methods of governance there.
#Icebreaker Series - Unicorn Riot series on ICE policy manuals
- Icebreaker Pt 1 – Secret Homeland Security ICE/HSI Manual for Stripping US Citizenship (Feb. 14, 2018)
- Icebreaker Pt 2 – Confidential Homeland Security Asset Forfeiture and Search and Seizure Handbooks (Feb. 22, 2018)
- Icebreaker Pt 3 – Confidential Homeland Security Fugitive and Compliance Enforcement Handbooks (Feb. 28, 2018)
- Icebreaker Pt 4 – Homeland Security Special Agent On-the-Job Training Manual (Apr. 27, 2018)
- Icebreaker Pt 5 – Confidential Homeland Security Undercover Operations Handbook (Jun. 22, 2018)
- Icebreaker Pt 6 – Leaked ICE Special Response Team Handbook for Planning and Executing Armed Raids (Sept. 18, 2019)
- Icebreaker Pt 7 - ICE Case Management Handbook Based on Federal Law Enforcement "System of Systems” (Dec. 13, 2019)
- Icebreaker Pt 8 – Leaked ICE Handbooks for T and U Visa Application Investigations (Dec. 18, 2019)
- Icebreaker Pt 9 – Leaked Interrogation and Arrest ICE Manuals (Jan. 1, 2020)
- Icebreaker Pt 10 – Leaked ICE Agent Private Bill and Commercial Trade Fraud Investigation Handbooks (Jan. 4, 2020)
- Icebreaker Pt 11 – Bush/Clinton Era Customs Investigators Manuals (Feb. 13, 2020)
Where did TECS tech come from?
Before ICE, a number of agencies used TECS to track suspects and in some cases post lookout notices for wanted fugitives. It was initially built under the Treasury Department primarily to track activity at U.S. borders and ports, and slowly expanded until many different agencies managed records in it.
Modernizing the 1980s mainframe-era TECS platform has been a recurring headache for IT administrators and Congress. The Government Accountability Office (GAO) produced a report in 2013 which outlined both the deep reliance on TECS and the necessity of replacing it with more modern systems.
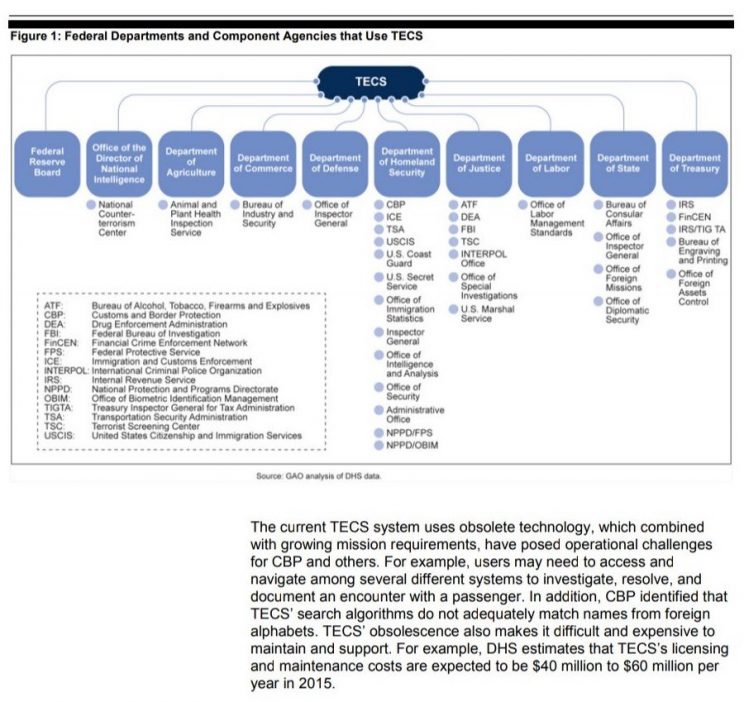
In 2014, ICE redoubled its efforts to refurbish TECS after previous attempts to streamline it, and managed to get it integrated with a reported 80 other federal databases. A 32-page “statement of objectives” published by ICE that year showed the major internal features of TECS and what improvements the agency hoped an outside contractor could perform on the system.
Various subsystems have been tacked onto TECS since ICE’s formation. One of the most important of these, particularly for travelers facing security screenings, is U.S. Customs and Border Protection’s (CBP) Analytical Framework for Intelligence (AFI), which could be dubbed the DHS system for ‘extreme vetting‘.
The Electronic Privacy Information Center (EPIC) has pursued a number of legal actions to find out more about TECS and AFI.
Intelligence contractor Palantir has won multiple sequential contracts to work on ICE case tracking. In 2014 the firm began overhauling TECS in a major ICE contract. More details surfaced in 2016 about Palantir, AFI and ‘extreme vetting.’
In 2017, Edward Hasbrouck writing for the Identity Project summarized the constellation of tracking systems:
“Palantir Tech is under contract with the DHS to build the Analytical Framework for Intelligence (AFI) for US Customs and Border Protection (CBP), and the Investigative Case Management (ICM) system for US Immigration and Customs Enforcement (ICE).
While development of AFI and ICM was commissioned by different DHS components, both are front-end data mining, data visualization, and data analytics modules for the TECS system, a ‘system of systems’ nominally overseen by CBP but used throughout DHS, by at least nine other Federal departments, and by state, local, and foreign ‘partners’.” — Edward Hasbrouck, The Identity Project
Hasbrouck also added that although some Palantir workers have defended their work based on a belief that it isn’t going to directly be involved in the targeting or deportation of migrants,
“both AFI and ICM are part of a long-term, high-priority TECS Modernization (‘TECS Mod‘) program specifically intended to eliminate this sort of data ‘compartmentalization‘ and make all government or commercial data available to any DHS component or other government agency available to all such components, so that they can better ‘connect the dots’ or establish guilt by association.“
In 2019, political controversies reached Congress as TECS-related systems and AFI-related facial recognition programs for travelers were proposed amid substantial opposition from legislators in both parties.
While the version of TECS that was critical to this edition of the manual has been phased out and replaced with Palantir’s ICM platform, this manual still provides useful insights into ICE’s internal structures and management patterns. Traveler monitoring including facial recognition is just one example of key surveillance technologies built through the immediate successors to TECS, which is detailed more in the manual below.
How is ICE’s case management data utilized?
A lot of the manual focuses on how ICE agents can study case management data to generate patterns of activity that can be managed statistically, which in turn are analyzed by third-party management consultants. ICE agents formerly used TECS to log their different types of activities, open and close cases, and keep records of their time sheets. In some cases, these data are also aggregated into reports that may show quantitative patterns about privacy.
One example of how case management aggregation leads to oversight analysis reports was when on February 1, 2017, the Department of Homeland Security Office of the Inspector General (DHS-OIG) released a report along with notes of a KPMG audit detailing how ICE spent federal drug control money in fiscal year 2016.
The report mentioned that there were some issues when ICE’s HSI transitioned from TECS into the new ICM system, noting, “The first release took place in the summer of 2016, when nearly 11,000 HSI users were migrated over to ICM.” Further footnotes show that technical problems with TECS beleaguered their statistics-gathering efforts.
TECS also appears in privacy assessments such as this 2013 Privacy Impact Assessment for the ICE Office of the Principal Legal Advisor (OPLA) Case Management System (OCMS). Privacy impact assessments are supposed to explain the privacy implications of different technologies as required under the Privacy Act. The report suggests that one day, data from different cases may be shared through an inter-connected system:
“CBP’s TECS system is a source of information in OCMS including, but not limited to, arrival and departure records, Reports of Investigation (ROI) from ICE HSI, biographic information regarding aliens, previous encounters of aliens at the borders, and fingerprint history on aliens including any criminal history or hits on their fingerprints.
Currently, OCMS users manually search this system and manually input any relevant data into OCMS, but eventually these systems may be directly connected to share data. The information collected from this system is used to support immigration-related cases and projects.”
In 2016, as ICM was rolled out across ICE in order to phase out the earlier generation of TECS, a privacy impact assessment laid out a lot of the key features and functions of ICM and how it would soon replace TECS.
In addition, a 2018 privacy impact assessment titled “ICE Parole and Law Enforcement Programs Unit Case Management Systems” covers the newer ICM era and additional newer databases created long after the case management handbook below.

What role did TECS play in the Boston Bombing and Wikileaks investigation?
While TECS has generally not been spotlit in news coverage since it was initially implemented in the 1980s, two cases brought certain features of TECS to light. Although the better-known post-9/11 ‘terror watchlist‘ system is known as Terrorist Identities Datamart Environment (TIDE), TECS has been used for decades as a key component of border security.
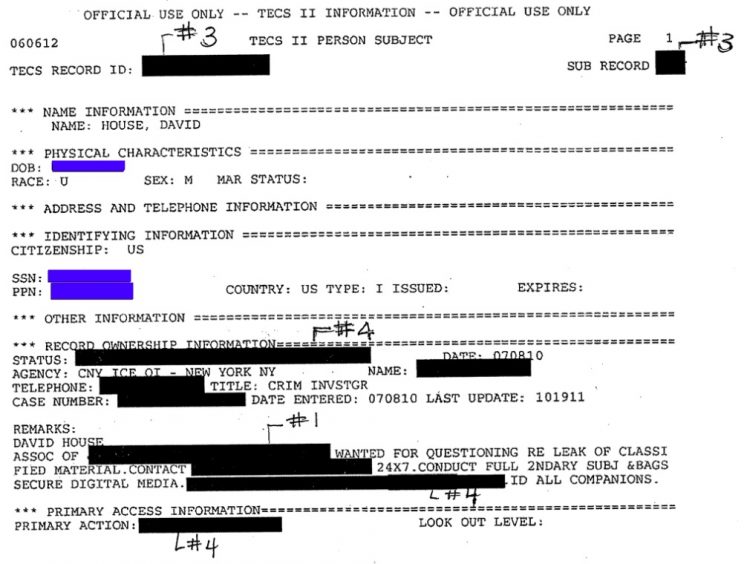
The most well-documented use of TECS’ lookout function in the ICE era, absent direct evidence of criminal activity, was against David House, a volunteer and supporter of the Wikileaks project for some time. In 2010, after a lawsuit forced its disclosure, the public learned that TECS had been used by ICE OI in New York City to place a lookout flag on House, a friend of Chelsea Manning.
In March 2019, House testified under subpoena to the grand jury proceeding aimed at Wikileaks; this is believed to be connected to the grand jury currently detaining Manning and Jeremy Hammond in an attempt to compel testimony.
After the April 2013 Boston bombing, officials reviewed the previous scrutiny aimed at the Tsarnaev brothers and eventually disclosed certain notices placed in TECS related to the attack. A partially-declassified Homeland Security congressional report shared a number of details about how TECS and TIDE had been used and should possibly be reformed.
Local media reports scrutinized Tamerlan Tsarnaev’s actions; while under the TECS alert flags, he was still easily able to get through U.S. border controls less than two years before the attack.
An “unclassified summary of a 168-page classified report […] by the Inspectors General for the Intelligence Community, Central Intelligence Agency, Department of Justice, and Department of Homeland Security” about the Boston Bombing also discusses the TECS alert flags in detail.
The role of TECS in ICE activity hasn’t passed entirely under the radar. The late actor Peter Fonda made a comment connecting TECS and ICE on Twitter, a subject rarely addressed.
Details of the Case Management Handbook
There are 61 page numbers in the PDF. Pages referenced below are not the embedded page numbers. Download the PDF directly here.
p2: Intro: This manual superseded a similar 2007 version.
Chapter 1: PURPOSE
p8: “This Handbook will assist enforcement personnel in opening cases, writing Reports of Investigation (ROIs), inputting and linking subject records, completing Seized Asset and Case Tracking System (SEACATS) Search/Arrest/Seizure (S/A/S) Incident Reports, posting hours, and posting enforcement and seizure statistics to cases in Case Management.”
p8: “The SEACATS is the system used to document all criminal and administrative arrests. The Enforcement Apprehension and Booking Module (EABM) and the Automated Biometric Identification System (IDENT) are the primary ENFORCE applications for OI SAs to use when processing arrests. […] The Integrated Automated Fingerprint Identification System (IAFIS) works in conjunction with IDENT. IDENT/IAFIS automates 10-print processing by enabling the electronic capture of 10- print fingerprints.”
p9: Case management is very important to resource allocation inside ICE.
p11: “A case may be opened when information is developed which indicates that a violation of one or more laws enforced by ICE has occurred or will likely be committed by specific individuals, organizations, or businesses. Cases can be opened for criminal and/or administrative purposes. In addition, cases are opened to assist other ICE offices, other federal, state, local, or tribal agencies, or foreign countries in enforcing their laws and regulations.”
p12: “A consensual intercept is the electronic monitoring of private communications with the consent of at least one party to the conversation. Consensual intercepts do not require a court order. For Case Management purposes, consensual intercepts are case statistics and are captured via the Electronic Surveillance (ELSUR) report.”
p13: “ENFORCE is a suite of applications designed to interface with the Enforcement Integrated Database (EID) for processing immigration enforcement related activities. Some of the systems include the ENFORCE EABM, General Counsel Electronic Management System, IDENT, and Worksite Enforcement Activity Reporting System (commonly referred to as LYNX). […] ENFORCE Apprehension Booking Module: EABM (formerly known as the Enforcement Case Tracking System) is the principal user interface with the EID, and is an incident-based application that standardizes the collection and reporting of immigration enforcement data across DHS.”
p14: “OI-Sponsored Organized Crime Drug Enforcement Task Force (OCDETF) Investigation: OI-sponsored OCDETF investigations are those that have been presented to and approved by an OCDETF Core City Coordination Group based on a proposal that was either formally sponsored or co-sponsored by an OI SA. For Case Management purposes, OI-sponsored or co-sponsored OCDETF investigations are case statistics.”
p16: “An offer in compromise occurs when a subject or business voluntarily agrees to pay duties and/or penalties, either prior to or after the issuance of a penalty notice by a U.S. Customs and Border Protection (CBP) Office of Field Operations (OFO) Director, Field Operations (DFO). Voluntary tenders are reported in Case Management as offers in compromise. For Case Management purposes, offers in compromise are final enforcement statistics.”
p18: “TECS-II is an automated enforcement and inspection system designed to support DHS, the Department of the Treasury, and other federal users.”
Chapter 3: ROLES AND RESPONSIBILITIES
Includes a lot of management directives about quality control, collecting time logs, case files and evidence therein.
p21: “First-line supervisors are in the best position to evaluate the necessity of collateral requests to other offices. Supervisors should not normally request that other SAC offices do things that can be done in their own office (e.g., requesting that other offices conduct TECS-II, National Crime Information Center (NCIC), or National Law Enforcement Telecommunications System queries, or queries for telephone subscriber information).”
p22: “Case Management in TECS-II automatically generates case review notifications.”
p24: Case initiation includes: Case Number Assignment, Investigative Case Categories, Types of Investigations, Vehicle Accident Investigations, Distribution.
p25: Case numbers are based on factors including office codes and fiscal years. “OI activities are reported in TECS-II Case Management using three broad areas: investigation; interdiction and intelligence gathering; and non-investigative (administrative).”
p26: The four types of investigations: General Investigative Activities, Formal Investigations, Collateral Investigations
and Investigative Referrals.
p27: “Examples of Collateral Case Numbers: TU02BR07DT0090-Collateral Office / DT02BR07DT0090-Originating Office”
Chapter 4: INVESTIGATIVE CASE FILES AND TECS-II REPORTS
p28: “TECS-II generated reports and records, except those excluded in other sections of this handbook, must be printed and included in the case file. […] Significant Event Notification (SEN) records should be printed out and included in the case file”
p29: “The TECS-II case record should be printed and attached to the inside of the case file on the left-hand side.”
p30: Some special designators such as “Updating Other Special Interest Fields (Joint Terrorism Task Forces (JTTFs), Title 21, etc.)” and “TECS-II Link List”.
p31: “ROIs describe the who, what, where, when, how, and why of an investigations. ROIs should be written in the third person. The author should not use indeterminate or passive language.”
p31: “The first page or synopsis of all ROIs containing information provided by confidential sources of information must be included in the source file. Initial source documentation ROIs must contain specific information that has been provided by the source. Every report that refers to a documented informant should be referred to by the assigned informant number and a copy should be placed in the source file.”
p32: “The first page of the ROI is the synopsis. The purpose of the synopsis is to provide the reader with an overview of the investigation and the purpose of the report.”
p32: “The removal of ROIs from the TECS-II Case Management is conducted only in the most extreme situations, such as those that may compromise the integrity of an undercover operation or threaten the life of an officer or an informant.”
p33: “The removed ROI number will not be reissued to a subsequent ROI. Defense attorneys and others will be able to recognize that an ROI is missing when they are provided with a group of sequentially-numbered ROIs during the discovery process. ROIs will not be removed due to factual, spelling, or grammatical errors.”
p33: “Classified Information and Certain Sensitive Documents: Classified information will not be included in any ROI or document within TECS-II. SAs need to be cognizant of the fact that certain sensitive documents are not to be included in the case file or referenced in ROIs (i.e., sensitive ICE, FBI, Drug Enforcement Administration, Department of Defense (DoD), financial documents, etc.). […] The SEACATS Incident Report is used to document arrest and seizures. The information is then transferred to Case Management. Enforcement activities that are reported in SEACATS (S/A/S) Incident Reports must also be reported in ROIs. […] The TECS-II generated Privacy Act disclosure report is used to document the disclosure of information on individuals who are the subject of a TECS-II subject record. The disclosure report is associated with the applicable TECS-II subject record. A separate TECS-II disclosure report must be completed for each individual who is the subject of a Privacy Act disclosure. If a disclosure which is reportable under the Privacy Act is made, then a Privacy Act Disclosure Report must be completed, printed, and filed in the case file.”
p34: “Subject records are created in TECS-II to document OI interest regarding persons, conveyances, and businesses. Subject records are linked in TECS-II to source documents such as ROIs and SEACATS (S/A/S) Incident Reports.”
p34-35: “Use of Digital Technology in Case Management. OI personnel are encouraged to use digital imagery whenever possible and practical. Imagery technology allows photographs, documents, and digital images to be stored and later viewed via specialized TECS-II terminals. Photographs of suspects and vehicles can be linked to TECS-II subject records.”
p35: “TECS-II generated intelligence reports are created by intelligence personnel within OI to document the collection and/or analysis of intelligence. Typically, these narrative reports are used to document intelligence that is not related to a specific OI investigation.”
p35: “The TECS-II generated ELSUR is used to request authorizations, grant authorizations, and transmit reports of use for consensual electronic surveillances. The ELSUR is typically initiated by the case officer and subsequently transmitted for approval to the first-line supervisor and the appropriate PHO. The ELSUR, like other TECS-II documents, is linked to the case record and subject records. It also becomes part of the electronic case file in Case Management. The ELSUR is used for both telephone and non-telephone consensual surveillances. SAC or designee approval must be granted prior to conducting non-telephone and telephone consensual electronic surveillances. An ELSUR request for authorization must be submitted for both exigent and non-exigent consensual non-telephone electronic surveillances.”
p36: “The Confidential Source Payment and Benefit Transaction Receipt (ICE Form 73-293) is used to document payments for information or evidence (POI/POE) and for other related expenses. Typically, the controlling SA or the case officer initiates ICE Form 73-293. A justification document (i.e., ROI or memorandum) must be included with ICE Form 73-293 and placed in the source file, but will not be maintained in the case file. Note: Payments/amounts to confidential informants are NOT documented in ROIs, only information or the action(s) of the source.”
p36: “The notes taken by informants to assist in their reporting of information to a case officer must be preserved in the case file.”
p36-37: “Rough draft ROIs need not be retained unless the rough draft is the enforcement officer’s first written record of an interview or surveillance. When this occurs, the rough draft itself becomes the officer’s original notes and must be retained. Conflicting information within these notes or between the notes and the ultimate ROI will likely be exploited by the defense. Therefore, note taking must be done with care. The OI SA must be prepared to explain any inaccuracies or contradictions that exist.”
p37: “Grand Jury Material must be handled in accordance with the procedures outlined in Rule 6(e) of the Federal Rules of Criminal Procedure.”
p37: “Fingerprints of subjects arrested by enforcement personnel will be recorded in IAFIS, if available, or on a minimum of two Criminal Fingerprint Cards (FD-249) and one Final Disposition Report (R-84). If IAFIS is not utilized, one of the criminal fingerprint cards will be mailed to the FBI for classification and storage.”
p38: “The Memorandum of Information Received (MOIR) is the method used by CBP officers, CBP import specialists, and other personnel to document information relating to violations of law that are enforced by ICE and CBP.”
p38: “The Fugitive Report is typically completed on all ICE OI fugitives by the case officer and subsequently approved by the SAC or designee.” See Icebreaker Part 3 for more information.
p39: “The proper storage of original case files is a critical factor in maintaining the integrity of the case and the viability of subsequent actions within the criminal justice system. Any document in the original case files may be used as evidence during judicial proceedings. Although not all discovery motions are granted to defense attorneys, case officers must remember that the contents of the original case files may ultimately be disclosed to the defense. If the contents of the original case files have been lost, altered, or otherwise handled inappropriately, the entire case may be dismissed.”
p40: “Any release of investigative case file material containing identifying data on a U.S. citizen or a legal resident alien to persons or agencies outside DHS (e.g., to other federal agencies), whether verbal or written, is required to be documented utilizing the TECS-II generated Privacy Act Disclosure Report.”
p40-41: “TECS-II subject records will be created for all individuals over the age of 14 who have been criminally charged or are the subject of an OI investigation. At the direction of the SAC, subject records may be created for individuals under the age of 14 for the same circumstances.”
p41: “A subject record will be created in ENFORCE for all subjects arrested for an immigration violation regardless of age.”
Chapter 5: ENFORCE
p41: “EABM and IDENT are the primary ENFORCE applications for OI SAs to utilize when processing arrests. IAFIS works in conjunction with IDENT. IDENT/IAFIS automates current 10-print processing by enabling the electronic capture of 10-print fingerprints. EABM/IDENT/IAFIS are used to capture biographic information and biometric identifiers for all subjects arrested by OI personnel. These systems provide the arresting officer with access to photographs and fingerprints for inclusion in the case file.”
p42: “All arrests of individuals (excluding juveniles under the age of 14 unless approved by the SAC) will be processed using EABM/IDENT/IAFIS. Subjects can be processed either by using an IAFIS live scan machine, or by using a flatbed scanner and hard copies of the fingerprint cards and photographs.”
Chapter 6: MANAGING HOURS AND STATISTICS
p42: “PHOs/SACs and other personnel use management information reports generated from TECS-II for a variety of reasons. These reports can be used to evaluate the performance of enforcement programs and offices, and are used by Headquarters personnel when responding to requests for information from external agencies. SACs use these reports to evaluate the performance of their offices, groups, and specific individuals. The information contained in Case Management standard reports is derived from the hours, statistics, and reports generated by TECS-II. Each month, SAs manually enter their hours from the previous month.”
p43: “The Executive Information Reporting Section (EIRS) of the OI Executive Information Unit is the primary point of contact for the generation of all executive level statistical reports. All requests for ICE data and/or statistics from agencies or entities external to ICE should be routed to the EIRS in order to ensure consistency, uniformity, and accuracy of statistical data.”
p43: “The Management Information System (MIS) module enables users to view and print reports from TECS-II. There are currently over 200 daily, weekly, monthly, quarterly, and yearly reports covering many different TECS-II, ICE, and CBP activities. These reports summarize information from several databases in TECS-II and can be used for audit applications. Several reports describe the current status of the database records, some summarize enforcement results, and others indicate the level of field usage of TECS-II. A major report is the SEACATS (S/A/S) Incident Report summarizing the searches, arrests, and seizures made by ICE and CBP personnel, by location or group of locations, for a variety of time cycles.” Also case hours are managed in TECS-II.
p44: A lot of information about how hours are tracked inside ICE-HSI. “OI SAs, Intelligence Research Specialists/Analysts, Seized Property Specialists, Forensic Auditors, Investigative Assistants, Technical Enforcement Officers, and other enforcement personnel as instructed by the SAC/PHO must post all their hours in TECS-II whether case-related or administrative in nature. OI personnel occupying support positions, such as Administrative Officers, Mission Support Specialists, Mission Support Technicians, Student Aids, Management and Program Analysts, Management Information Specialists, Management Program Technicians, Enforcement Support Specialists, Secretaries, etc., are not required to post their hours in TECS-II. State and local law enforcement personnel, National Guard, and Department of Defense (DoD) employees serving in an ICE office or on an ICE task force will not enter hours in TECS-II.”
p44-45: “Undercover Hours: Enforcement personnel who perform in an undercover capacity are required to enter these hours in Case Management in the appropriate columns that are identified for undercover use only. Hours that are reported in the undercover columns are not to be reported in the non-undercover hours columns. Hours are undercover or not undercover, never both. Enforcement personnel will report hours as being attributable to undercover work only when they were actually in an undercover role. Translating audiotapes of undercover meetings, writing reports on undercover activities, and participating in security surveillances of undercover meetings will not be reported in Case Management as undercover hours. Supervisors who review the hours of undercover personnel must ensure that the number of these hours is reasonable and that they were actually spent in an undercover role.”
p45: Icebreaker Part 6 looked at certain issues involving administratively uncontrollable overtime (AUO). “Uncontrollable Overtime (UOT): Law Enforcement Availability Pay (LEAP)/Administratively Uncontrollable Overtime (AUO). SAs who work LEAP hours or enforcement personnel who work AUO must enter their hours in the Uncontrollable Overtime (UOT) column in TECS-II.”
p46: Collecting statistics and using TECS-II email to help with that.
p47: “Enforcement personnel are required to provide final dispositions for all initial enforcement activities (e.g., arrests, seizures, penalties issued, etc.). Each initial enforcement statistic must have a final disposition associated with it before the case status can be set to “closed” in Case Management.”
p49: “Investigative Case File Folder Go-by”. A template for a case folder. Includes dividers for court documents and case documents.
p59-61: List of acronyms.
#Icebreaker Series - Unicorn Riot series on ICE policy manuals
- Icebreaker Pt 1 – Secret Homeland Security ICE/HSI Manual for Stripping US Citizenship (Feb. 14, 2018)
- Icebreaker Pt 2 – Confidential Homeland Security Asset Forfeiture and Search and Seizure Handbooks (Feb. 22, 2018)
- Icebreaker Pt 3 – Confidential Homeland Security Fugitive and Compliance Enforcement Handbooks (Feb. 28, 2018)
- Icebreaker Pt 4 – Homeland Security Special Agent On-the-Job Training Manual (Apr. 27, 2018)
- Icebreaker Pt 5 – Confidential Homeland Security Undercover Operations Handbook (Jun. 22, 2018)
- Icebreaker Pt 6 – Leaked ICE Special Response Team Handbook for Planning and Executing Armed Raids (Sept. 18, 2019)
- Icebreaker Pt 7 - ICE Case Management Handbook Based on Federal Law Enforcement "System of Systems” (Dec. 13, 2019)
- Icebreaker Pt 8 – Leaked ICE Handbooks for T and U Visa Application Investigations (Dec. 18, 2019)
- Icebreaker Pt 9 – Leaked Interrogation and Arrest ICE Manuals (Jan. 1, 2020)
- Icebreaker Pt 10 – Leaked ICE Agent Private Bill and Commercial Trade Fraud Investigation Handbooks (Jan. 4, 2020)
- Icebreaker Pt 11 – Bush/Clinton Era Customs Investigators Manuals (Feb. 13, 2020)
Please consider a tax-deductible donation to help sustain our horizontally-organized, non-profit media organization:



